
IAM for cyber insurance
Cyber attacks are real! – Are you insured?
Cyber insurances are one building block in the IT security concept of businesses, but they do not only provide Insurance coverage, instead they also place demands on the IT security of businesses.
Bitkom
Damage per year for
German businesses in 2022
203 Bn €
Verizon
Wordlwide cyberattacks involve credentials (including Brute Force and Phishing)
61 %
Cybersecurity Insiders
Organizations say passwordless MFA is important to stop credential-based attacks
91 %
Identity & Access Management as main pillar within a cyber insurance
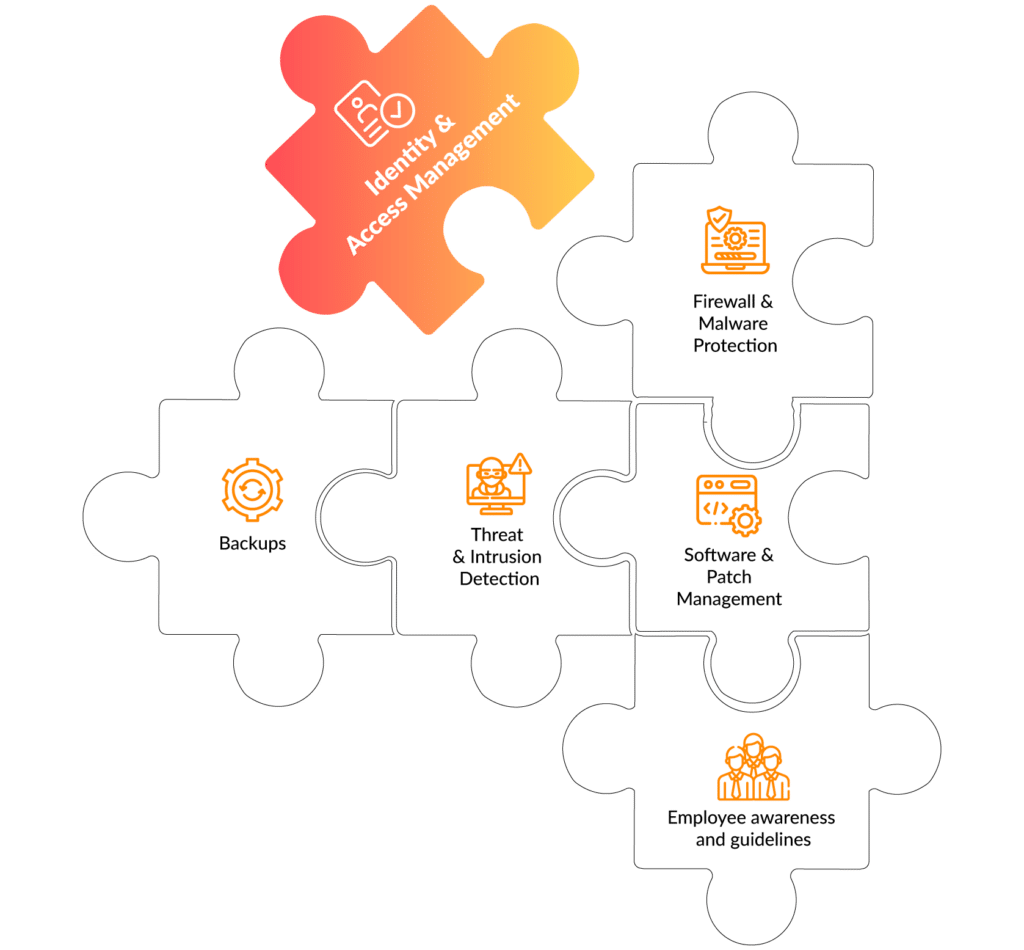
Many cyber insurances place demands on the IT security of businesses to reduce the risk of cyber threats and thereby also optimize the risk of their portfolio. The requirements to businesses often include Multi-Factor-Authentication, fine-grained authorization management as well as threat and intrusion detection. Since compromised user accounts are a major threat for businesses, a modern Identity & Access Management solution is a main pillar within a cyber insurance. It provides capabilities to manage the user identities, including the lifecycle, as well as provides features such as Multi-Factor-Authentication, Authorization management and more over can provide useful data and events to threat and intrusion detection solutions.
Business Continuity
Backups & Data Recovery (BCM)
Backups are crucial for business continuity and to restore business operations as well as prevent data loss in case of a cyberattack.
Authentication & Authorization
Identity & Access Management
Identity & Access Management provides unified user management with secure authentication and end-to-end authorization.
Security Training
Employee awareness and guidelines
Raising employee awareness and binding security guidelines can significantly reduce the human element as a risk factor.
Software Updates
Software and Patch Management
Up-to-date software prevents known vulnerabilities from being exploited and thus reduces the attack surface dramatically.
Security Monitoring
Threat & Intrusion Detection
By detecting a security incident at an early phase, countermeasures can be initiated quickly and the attack can be contained at an early stage.
IT Infrastructure
Firewall & Malware Protection
By using security applications such as firewall and malware protection, many cyber attacks can already be prevented or detected.
Identity & Access Management
provides what a Cyber Insurance demands
Multi-Factor-Authentication
Multi-Factor Authentication is one of the most commonly requested requirements for a cyber insurance policy. Multi-factor authentication (MFA) uses at least two different authentication factors, such as a password and a TOTP code, to provide strong user authentication. In this way, user accounts are more secure and the risk of a compromised account as entry point of a cyber attack is significantly reduced.
cidaas offers extensive authentication options, for passwordless as well as multi-factor authentication. In addition, cidaas provides with its SMART MFA capabilities a risk-based multi-factor-authentication, so that the additional factor is only requested in case of suspicious behavior.
Authorization
Authorization is the management and enforcement of access rights, e.g. which applications or functionalities a user may or may not access. Authorization is therefore often an essential requirement in the context of cyber insurances. It must be ensured that users do only possess the permissions they should have and cannot obtain them by fraud (privilege escalation) in order to prevent unauthorized access.
cidaas offers an extensive group and role management as a basis for authorization. The authorization is enforced in cidaas as well as shared with integrated applications. Furthermore, changes in the authorizations can be tracked via various reports and activity streams so that unusual changes can be addressed quickly.
Identity & Access Management as a core building block within a cyber insurance: Multi-Factor-Authentication
Take a look at our latest blog on the role of Multi-Factor-Authentication as a core building block within a cyber insurance. Why do cyber insurances request it and what benefits can it provide to the overall IT security setup of a business.

Frequently Asked Questions
Does my business need cyber insurance?
Cyber insurance protects against the damages from a cyber-attack, and is a safeguard for businesses to receive financial assistance or other offers of help in the event of an emergency. Whether cyber insurance is necessary for one’s own company or not should be weighed up based on the individual requirements in the company. The criteria include in particular the probability of a cyber-attack and the extent of the potential damage, other factors such as the industry and company size, as well as the already-established IT security concept are used as criteria. However, customers or partners, as well as regulatory requirements require nowadays more often a cyber insurance. In general, a cyber insurance should be integrated into an overarching IT security concept in order to provide the best possible protection.
Why do cyber insurance companies require multi-factor-authentication?
Multi-factor-authentication ensures secure authentication and thus reduces the risk of a user account being compromised, which is one of the biggest risks in context of cyber-attacks. The most common cause of a compromised user account is the misuse of access data, especially the password, which is obtained via phishing, for example. Insurance companies therefore mandate the use of multifactor authentication, at least for certain areas or user groups, in order to reduce this attack vector and thus the risk.
Is Identity & Access Management important for cyber insurance?
Identity & Access Management is an important solution for IT security. Therefore, cyber insurances also often require at least some features that are part of an Identity & Access Management. Two of the most frequently mentioned requirements in cyber insurance are multi-factor-authentication and authorization management. In addition to these two functionalities, a consistently implemented Identity & Access Management provides much more, ranging from a Single Sign-On to consistent monitoring of user access. Identity & Access Management is therefore not only elementary for the IT security concept, but also for cyber insurance.


