
Digital identity verification – anywhere, anytime
What is an identity check?
First and foremost, identity verification is performed to ensure that a person really is who he or she claims to be. Identity verification is an essential prerequisite for most online and offline processes and procedures, for example, when opening accounts, concluding contracts, official procedures, and security checks. But it is also used to verify a person’s age, which has long been practiced in local commerce in particular but is also becoming increasingly present in e-commerce when it comes to purchasing products that require a certain minimum age.
Identity verification – online?
First of all, it is important to know that there are different regulations and rules for digital identity verification, which provide frameworks for different industries and applications. This is primarily to counter identity theft and counterfeiting and fraud maneuvers.
For banks, there is the Money Laundering Directive (AML5 – Anti Money Laundering), which aims to combat money laundering, terrorist financing and identity fraud. In this context, KYC (Know your Customer) is also frequently discussed.
In addition, there is the Telecommunications Act (TKG), which forms the legal framework for the telecommunications market. In 2021, this was supplemented by the Telecommunications and Telemedia Data Protection Act, which provides for the identification of digital persons.
In Europe, the eIDAS Regulation (electronic IDentifictaion, Authentication and trust Services) is of particular importance, as it forms the European legal framework for electronic identification.
Digital identity verification procedures in the transition to digitalization
The development of identity verification has undergone a remarkable transformation in recent years. Previously, physical presence and personal identification documents were the main tools to verify a person’s identity. However with the advent of digital technology, this process has changed significantly, and a wide variety of identity verification procedures have been developed over time.
The following is an overview of the procedures:
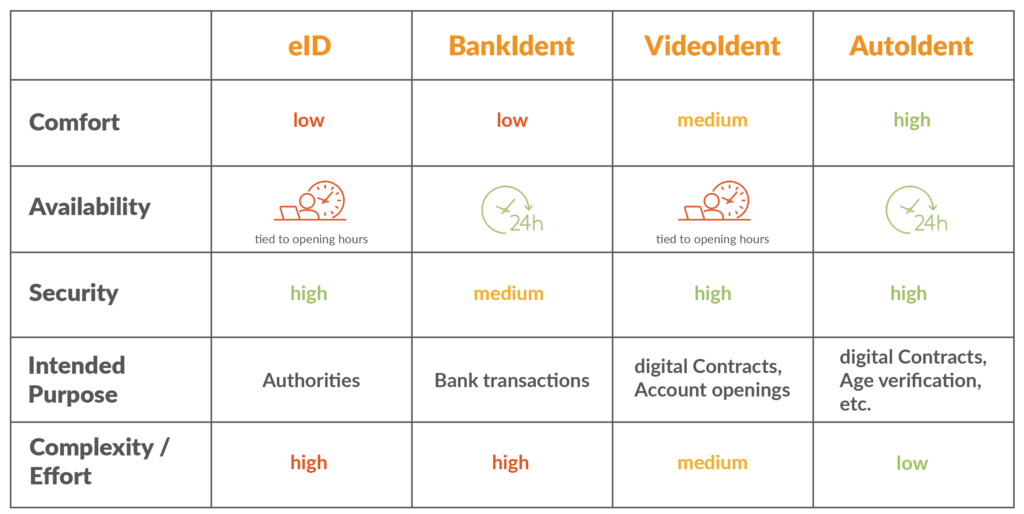
eID
Identification by means of eID refers to the use of an electronic ID card or electronic identity card (ePA) to verify a person’s identity – by means of integrated chips, with various personal information stored. This is inserted into a reader or read wirelessly via NFC (Near Field Communication). The problem here, however, is that there are only limited ways to use the eID.
BankIdent
BankIdent is a procedure for identifying customers in banking transactions. It enables secure and fast identification via online banking. The procedure involves photographing their identification document as well as their face. After logging into the personal online banking system, an automatic 1-cent transfer is initiated for final identification, which must be confirmed by entering a TAN. Transfers at the weekend will not be booked until the following working day.
VideoIdent
VideoIdent is an online procedure that allows customers to identify themselves by means of a video chat, regardless of their location. The customer only needs to have a valid ID ready and can then speak to a company employee via a video connection, who verifies the identity. The disadvantage is that the performance of the identity check by an employee is tied to predefined times.
AutoIdent
AutoIdent is an innovative solution for identity verification in the digital era. Using AI and machine learning, AutoIdent enables fast and secure verification of individuals. The method ensures a smooth process while protecting against fraud. The application is simple and easy to use, accessing the smartphone’s camera after the user’s consent and verifying identity data in real time. In contrast to VideoIdent, the identity verification with this procedure can not only be carried out independent of location but also independent of time, even the contact to another person is not required. The cidaas ID validator is based on this procedure.
Identity verification of the future – with the cidaas ID validator
With the cidaas ID validator cidaas enables you to check different identity documents comfortably & in real time. Hereby the already mentioned AutoIdent procedure is used, the fully automated, video-based legitimation. Users are guided through the identity verification process without having to interact with a third party.
In addition to a significantly more efficient cost structure, this also has a strong impact on the customer journey and ensures an optimal customer experience. The cidaas ID validator convinces not only by its user-friendliness but also by its highest security, which is shown among other things by the fact that the procedure is certified according to the eIDAS conformity guidelines.
How does the cidaas ID validator work?
The first step is the ID scan. The end user simply holds a suitable ID document in the camera, whereupon it is automatically classified. This means that the system itself recognizes what type of ID document it is. In the background, checks are performed based on various security features to verify validity. Personal and biometric data is extracted for analyzing authenticity and stored for later comparison with the facial scan data.


The next step is the face scan. For the digital identity check, the biometric data of the face scanned by the artificial intelligence is extracted. A randomized sequence of movements is also used to verify the authenticity of a person. This minimizes the risk of the system being duped using video recordings or deep fakes.
For the final confirmation of the identity, the analysis takes place in the background and directly after the face scan. This is an intelligent comparison of the extracted biometric data of the face and the ID card image. A comparison of the front and back of the ID card also takes place to determine data consistency. Users are thus guided through the process quickly and easily, while the authenticity of their digital identity is verified – in less than two minutes.

Advantages of digital identity verification with the cidaas ID validator
- Secure identification
AI algorithms ensure that authentication can proceed securely. In this way, machine learning can sustainably exclude disruptive factors, such as blurred images. But the models also learn about new attack scenarios and recognize potential identity theft. Artificial intelligence not only matches unique facial aspects of the ID card and the real person, but also checks whether the specific security features of the ID cards are present, such as holograms.
Another important factor of identity verification includes GDPR compliant processing of all personal data as well as eIDAS compliance during identity verification. - Unique, convenient user experience
It has never been easier and more convenient to verify oneself digitally because no contact with another person is required. Therefore, users benefit from the simple and fast verification process. Verification can thus be carried out at any time and in any place, on any camera- and Internet-enabled device. - Reduction of process costs
Companies save process costs noticeably with the cidaas ID validator. External manpower is reduced or even completely replaced, which significantly reduces the costs per identification case. Likewise, internal employees can increase their work efficiency through targeted customer support. The entire process flow becomes more efficient through the immediate provision of the data obtained from the analysis in the right systems.
Digital identity verification will continue to gain in importance in the future. It offers an efficient and secure method of verifying people’s identities online. This enables companies to prevent fraud and strengthen customer trust. Using technologies such as machine learning and artificial intelligence, identity verification is becoming increasingly accurate and reliable. However, data protection and privacy must be ensured to prevent misuse. Overall, digital identity verification is an important step towards a secure and trustworthy digital world, as already demonstrated by a wide variety of existing use cases, such as digital contracts, driver’s license verification, age verification or onboarding processes.
Learn more about the features of the cidaas ID validator in upcoming blog posts. Learn about different use cases and other arguments in favor of using the cidaas ID validator and how to increase people’s trust towards digital identity verification.
Get even more insights on the cidaas ID validator in our webinar “The role of trust and trust services – digital identity validation“.
