Federated identity management for the SAP Business Tech Platform – done right with cidaas
A standards-based approach to seamless access control and role mapping with SAP BTP and cidaas.
As organizations move deeper into SAP’s cloud ecosystem, especially the SAP Business Technology Platform (BTP), federated identity becomes a foundational requirement. The days of managing user credentials and roles directly within each application are over.
Instead, authentication and access control are externalized. Trusted identity providers ensure secure login, token issuance, and role-based access via open standards.
Here, cidaas offers a compelling, cloud-native alternative to traditional monolithic identity systems. cidaas is based entirely on protocols such as OIDC, SAML, and SCIM and can therefore be seamlessly integrated into SAP’s cloud stack.
This includes flexibility, scalability, and complete data sovereignty in the EU.
Federated identity management (FIM) vs. single sign-on (SSO)
Although single sign-on and federated identity management are often mentioned in the same breath, they are two different concepts in modern identity management:
SSO allows users to authenticate themselves once and then access multiple applications within a security domain. They do not need to log in again. Typically, login information such as username and password is managed centrally. This increases productivity and user-friendliness and reduces the need for multiple passwords.
Federated identity management goes one crucial step further: It links different identity providers via trust-based federations so that users can be authenticated across multiple domains and systems. This allows organizations to centrally control access and authorization, even if resources are located in external networks or cloud environments.
Federated authentication protocols such as SAML, OIDC, or OAuth2 establish a trust relationship between the services involved. Tokens and assertions are transmitted to determine which permissions and roles a user has.
For example, a user can log in to an external identity provider and then gain access to SAP BTP or other applications. This eliminates redundant logins and separate password management.
Here is a clear summary of the differences between federated identity management and SSO:
| Comparison | Single Sign On SSO | Federated Identity Management FIM |
| Access | Within a domain | Across multiple domains & systems |
| Authentifizierung | Single Sign On | Trust-based federation |
| Identity provider | One central provider | Multiple providers (federated) |
| Protocols | Internal | SAML, OIDC, OAuth2 |
| Security | Simplified | Extended, standardized |
| Area of application | Internal applications | Hybrid & multi-cloud environments |
From identity to application access – The federation flow with cidaas
When connecting to SAP BTP, the identity flow follows a well-defined pattern. A user requests access, is authenticated through a centralized identity provider, and receives a token. This token includes claims that SAP BTP uses to determine which roles and permissions to assign. Der Vorgang läuft ab ohne den Benutzer lokal verwalten zu müssen.
With cidaas as the identity layer, this process becomes fully manageable and customizable. The platform not only authenticates users through secure login mechanisms (including multi-factor authentication and single sign on), but also defines the exact attributes and roles that should be included in each authentication token. These claims are then used downstream to map users into role sets and role collections in SAP BTP.
The result is a frictionless, secure login experience for the user – and fully automated, policy-driven access control for the organization.
Inside the federated identity management architecture
Let’s take a closer look at how cidaas handles federated access to SAP BTP in practice:
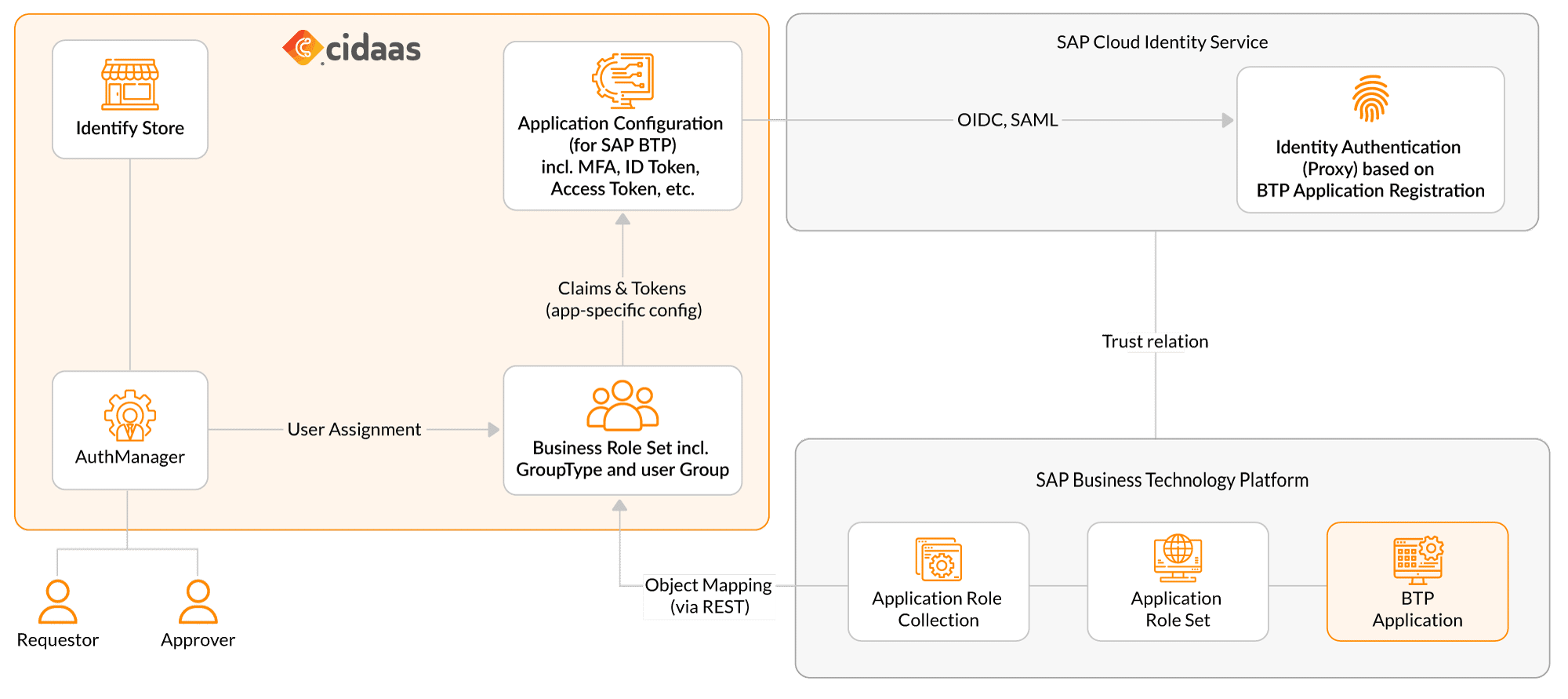
At the core of the federated identity management system is the cidaas Identity Store, where users, groups, and business roles are managed. This includes attributes like department, user group, or region — all of which can be used for role assignment.
The cidaas AuthManager handles authentication requests and MFA policies, while the Application Configuration defines what should be included in the access token for each target system. For SAP BTP, this typically includes group claims that reflect the user’s business role, which are then mapped to SAP-specific role sets and collections.
All of this is delivered via OIDC or SAML to SAP Cloud Identity Services, which acts as the authentication proxy for BTP. SAP BTP, in turn, trusts this identity source and applies the mapped permissions accordingly.
The entire mapping logic — from business roles in cidaas to role collections in BTP — is managed via RESTful APIs, ensuring that updates are automated, auditable, and scalable.
Technical deep dive: Tokens, assertions, and trust configuration
An important success factor in implementing federated identity management is the correct interaction of tokens, assertions, and trust configuration.
SAML or OIDC are used for authentication via federated systems. After successful login with the identity provider, a token is generated that:
- Confirms the identity of the user,
- Contains certain attributes or group information, and
- Specifies authorization for access to specific resources.
These tokens are then forwarded to the connected applications, e.g. SAP BTP. There, roles and authorizations are assigned based on the data contained in the assertion.
The trust configuration defines which identity providers are considered trustworthy and which policies are applied for processing. This trust relationship between provider and service is crucial for:
- Preventing misuse,
- Clearly separating security domains from one another,
- Speeding up the login process, and
- Simplifying data management.
With an API-first approach, such as that offered by cidaas, these trust configurations can be automated and flexibly adapted. Federated identity management is therefore ideal for companies that need a scalable identity infrastructure.
The benefits of this federated identity management approach
Using cidaas as the federated identity provider for SAP BTP brings multiple benefits:
1. Standards-first integration
cidaas is built from the ground up on open standards like OIDC, SAML, and SCIM. This ensures full compatibility with SAP’s modern identity model, including seamless integration with SAP Cloud Identity Services and support for custom claim mappings.
2. Clean separation of roles and tokens
With cidaas, the logic that determines who gets fine-grained access to what is fully externalized. Business roles can be defined independently of SAP-specific configurations, and mapped to application-specific tokens via a clean API-based interface.
3. Fine-grained control
cidaas allows for precise control over token contents, including user group attributes, role assignments, and dynamic claims. This is particularly important for organizations with complex role hierarchies or multi-brand environments, where access needs to reflect business context.
4. Full user experience customization
Unlike rigid enterprise identity systems, cidaas provides full flexibility to brand the login experience. Organizations can design tailored portals for different user groups (e.g. internal teams, external partners, suppliers) — all while applying consistent security policies.
5. Sovereignty and compliance
cidaas is hosted in Germany and Switzerland, certified to ISO 27001, and developed under strict GDPR compliance. For organizations in regulated industries or public sector environments, this offers peace of mind that identity data remains under full control.
Federated identity management real-world applications
The cidaas approach to federated access is already in use across organizations that require robust integration with SAP systems but want to avoid the complexity, rigidity, or sovereignty challenges of traditional identity platforms.
This architecture works equally well for:
- Enterprises moving from SAP IDM to a modern, cloud-first identity model
- Organizations needing external identity support (partners, customers, suppliers)
- Scenarios with mixed SAP and non-SAP landscapes
- Environments requiring flexible role mapping and access control
Thanks to its API-first design, cidaas can also be extended or combined with platforms like cnips, which provides process orchestration, workflow automation, and additional logic for access requests, approvals, and SoD risk handling — all while keeping the identity core clean and manageable. The core identity remains clear and manageable.
Let’s take it one step further, to a more technical level.
Could federated identity management become the standard?
The increasing use of the cloud, the expansion of hybrid IT architectures, and the growing number of distributed identity systems make federated identity management a logical next step for many organizations.
Identity federation offers companies the ability to flexibly authenticate identities across different domains and assign access centrally. At a time when SaaS services, partner networks, and external suppliers are an integral part of business processes, FIM is becoming a critical success factor.
FIM may seem a bit outdated from today’s perspective, but the importance of federation remains unbroken, and especially in scenarios of growing collaboration, hybrid environments, and complex processes, the technology behind it is more relevant than ever.
It is therefore very likely that it will become the de facto standard for managing digital identities in companies in the coming years, especially in conjunction with cross-platform solutions such as SAP BTP and modern cloud ecosystems such as cidaas.
Conclusion: Federated identity management – What´s next?
Federated identity is more than a checkbox for SAP BTP. It’s a strategic layer of your architecture that determines how users authenticate, how roles are assigned, and how access is controlled, across cloud applications, business units, and user groups.
With cidaas, you get a powerful, standards-based identity platform that puts you in full control. It handles authentication, token management, business role mapping, and integration with SAP – all while offering the flexibility, sovereignty, and simplicity modern organizations demand.
And best of all? It does it without locking you into one ecosystem or provider nor forcing you to compromise on compliance.
If you are interested in more details, please feel free to schedule a free appointment with our cidaas experts. We look forward to hearing from you! What’s Next?
In part 3 of our IDM blog series, we turn our attention from the topic of “federation” to the topic of “identity provisioning.”
Here, we take a look at how cidaas supports user lifecycle processes, connects to SAP Cloud Identity Services via SCIM, and seamlessly integrates into companies’ HR-driven identity workflows.
Did you miss part 1? You can find out more about “SAP IDM End of Life – Time to rethink identities” here.
