
Bye bye password – an easy way to passwordless authentication with cidaas
Let us not fool ourselves
Passwords have a long history, and a PIN (Personal Identification Number) is nothing else. They are used to authenticate the user in conjunction with predefined or self-created user IDs or, more commonly today, a communication address such as an email address or mobile phone number. The latter have the advantage that it is much easier to remember these user IDs, and they can also be used for communication. The password-based authentication method is also basically easy to implement. The secure storage of this data and also the administration of the authentication is unfortunately somewhat more complex.
Until recently – if you’re honest, still do it today 😉 – every device that you use and every portal required a user ID and, above all, a password from its users to set up the user account.
What have we achieved in IT with this?
- a supposedly simple, functioning login
- Much frustration for users who cannot remember passwords and have to go through cumbersome processes to reset passwords
- Users who write down their passwords/PINs in insecure places
- Style blossoms, such as password managers, with which users supposedly manage their passwords or PINs securely. It is important to know that a password manager can also be the target of hacker attacks. Access to the password manager is not necessarily secure and the encryption of the user IDs is always bidirectional because the passwords can only be applied in plain text
- A variety of daily hacker attacks that (want to) hack numerous portals with clever user ID + password combinations
(New) user authentication methods
In addition to the password, a number of other authentication methods have therefore been developed in recent years, ranging from one-time passwords (OTP) and push methods to the smartphone to device biometrics and FIDO2. Many of these procedures are already used today as multi-factor authentication and are therefore already familiar to many users. The procedures differ essentially in that one no longer relies on the knowledge factor, but rather on the factors of possession and inherence, and in particular a combination of both factors. These factors not only increase security, but also create a good and consistent user experience through convenient and simple passwordless authentication.
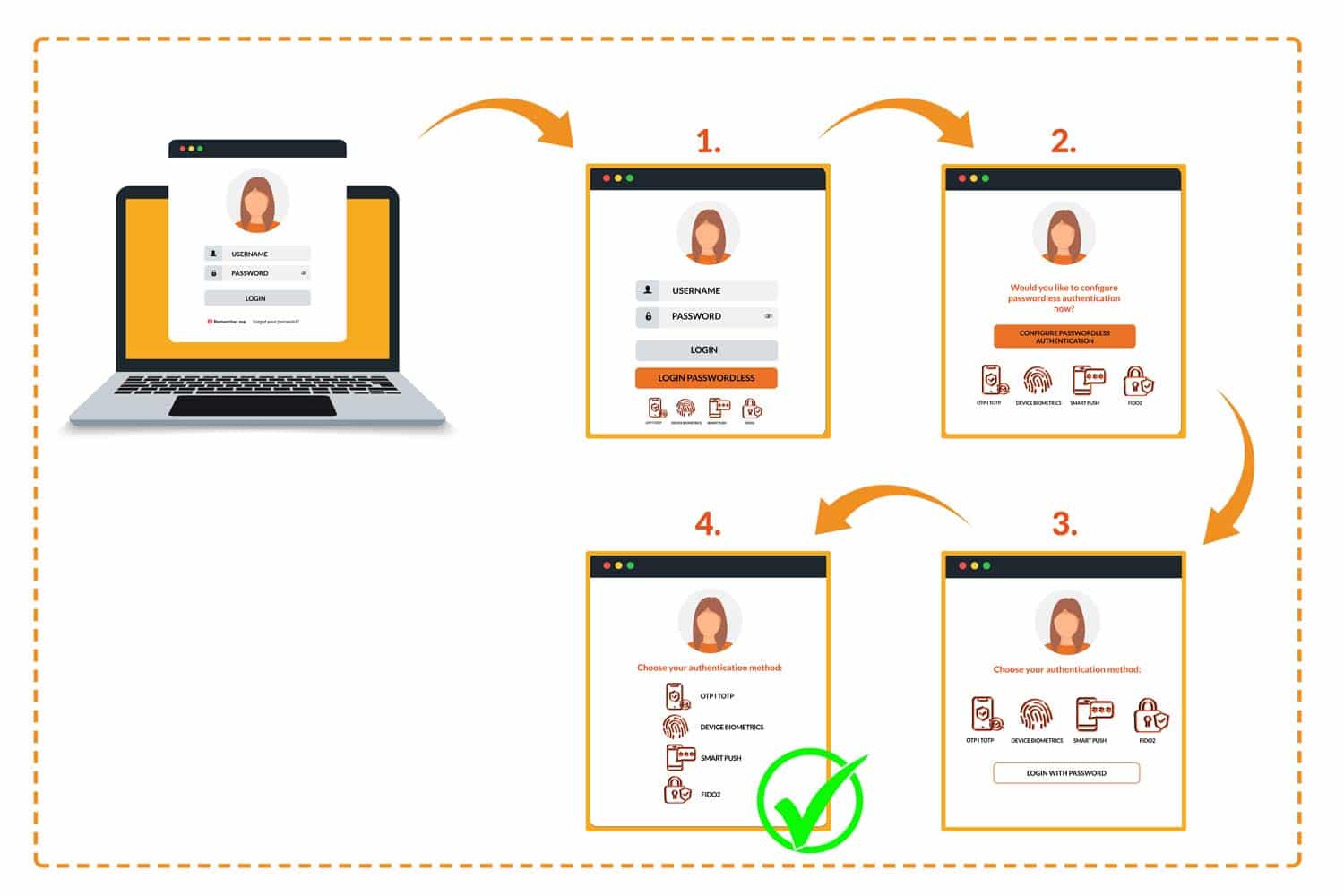
For many companies, the question now is how to establish passwordless authentication and enable users to switch from the password to, for example, FIDO2. While adoption of passwordless authentication depends on a variety of factors and varies by organization, use case, and audience, an underlying approach to adoption can be identified.
Many companies today rely on a classic login with a username and password, whereby the username in the vast majority of cases is the e-mail address.
- Offering passwordless authentication alongside the classic login with password enables a step-by-step introduction in which initial experience is gained and users can familiarize themselves with passwordless authentication. If multi-factor authentication is already in use, these procedures can be used directly as a passwordless alternative, e.g., an OTP via email or the push message to the smartphone.
- The configuration of the passwordless authentication procedures can be easily integrated into the existing login process to make users aware of the new authentication options and to onboard them.
- After a transition period in which users have gradually switched themselves to passwordless authentication, a switch to passwordless authentication only can be aimed at. The phasing out of the password can also be done step by step, e.g., by offering login with password as an option below the passwordless authentication.
- Passwordless authentication and the deactivation of the password are probably not yet conceivable for many companies today, but the last step of deactivating the password should also be considered in the vision. The deactivation of password-based logins should be announced well in advance in order to motivate even the last few users who have not yet switched to using passwordless authentication.
Always the same challenges
Sign-up
Some companies see a high risk when accessing their customers that the sign-up becomes too time-consuming or complex, which increases the churn rate. For other organizations, this may not be a reason because it is a necessary evil due to the user account that must be used as part of the overall service offering. For all companies, however, the risk of hacker attacks with user ID and password-based accounts is incredibly high, and it is only a matter of time before unauthorized access is possible.
Selection of alternatives
There are different alternatives for the implementation, depending on the current implementation of the user administration.
Very often, companies express the wish that they basically only want to introduce “2-factor authentication” to make accounts more secure or that they want to use appropriate Captcha technologies in the customer environment in order to at least be able to make simple hacker attacks more difficult. We refer to this approach as the “on-top approach” because it does not substantially change anything, but merely uses additional procedures.
However, this “on-top approach” has a number of limitations, because
- the user authentication is still carried out with user ID + password,
- usually only one or two alternative methods can be implemented for 2-factor authentication,
- the implementations tend to be bulky and quite expensive when additional hardware is needed.
In fact, the selection of alternatives should follow the following principles:
- In which direction are the authentication methods developing, which protocols and technologies do, e.g., end device manufacturers offer today?
- What user experience do your different users have with the authentication methods – is it really enough to offer one or two alternatives?
A very important point, however, is that users no longer use their user ID + password as the primary authentication method, so that hackers cannot work through their user management with user lists from dark channels.
Communication concept and user self-services for the changeover
Changing familiar processes is not always easy. For this reason, a simple and clear communication concept implemented in the software is part of every changeover.
Clear lines
Motivate your users to use alternative verification methods and provide the password only as a second option for multi-factor authentication.
- Use common and intuitive user verifications already at sign-up. Users can then gradually set up their verification methods.
- Do not force the setting of a password – use the password as an alternative method for 2FA, set up by the user.
- Allow their users a significant choice and configuration of verification methods – sure: a user will not activate all methods.
- Determine the verification methods to be used also based on the criticality of the applications.
- Motivate the user to set up a new, passwordless verification method when logging in, and remind him or her of this if necessary.
Conclusion
Passwordless authentication is the future and will over time replace traditional password logins. In addition to users choosing weak or predictable passwords, the increasing number of data leaks and phishing attacks have become a problem and major risk for passwords.
It is important for companies to take the step towards passwordless authentication today and to select suitable authentication methods depending on the use case and application in order to achieve the highest level of security and user-friendliness.
It is clear that we all still use passwords here and there today, be it in a private or business environment – and yes, sometimes they are the same passwords. But we must realize that there are already better and more secure alternatives to the use of passwords, or that we can at least increase security through multi-factor authentication – i.e., by using a second factor for authentication! We at cidaas therefore advocate passwordless login alternatives!
