Workforce IAM – The Evolution which is a Revolution: The (R)evolution of Workforce IAM
User provisioning – traditional approaches vs. modern ones
What does user provisioning actually mean?
Basically, it’s about making a user known to all the systems they use. In a slightly broader sense, it can also be said that a person who is hired is set up in a system, and this system, manages the person as a user and then arranges distribution to the further systems.

When do you need user provisioning?
- If a system needs to have all users in order to work correctly. These are usually systems that are used to manage people or tasks, such as payroll, project management.
- If a system requires a dedicated assignment of permissions to a user in advance, e.g., the assignment of a usage license, such as a collaboration platform.
In many systems, however, user provisioning is not needed if the user information is supplied at authorization (or login). The user is then linked in the system, if necessary.
The challenges of user provisioning
Providing users and possibly their authorization in other systems is an interface problem.
- The source system (QS) needs interfaces.
- Each target system (ZS) needs interfaces for retrieving, editing, and deleting users and authorizations.
- Then a mapping of the interface of the source system and the target system must be done in each case. It should be noted that the interfaces of the target system can change from version to version.
- Depending on the interfaces available, either
- either data is exchanged via a modern WebAPI,
- file interfaces are used,
- proprietary interfaces are used, or
- Data adapted directly in the target system’s database (usually a database).
Conventional user provisioning approaches
First of all, the tools still in use need to be considered, and an explanation of terms certainly helps, because the term Identity & Access Management (IAM) is often used somewhat ambiguously.
An IAM should implement an Identity Provider (IDP) and have all access management methods ready to perform user authentication.
Some vendors also title their product IAM, essentially providing user provisioning to various systems, including the various IDPs if applicable, and analytics. Other products offer more or less all functions.
Looking at the challenges outlined above, it quickly becomes clear that systems that proclaim to be able to connect to all possible systems in the world are either very generic and require a lot of customizing or would have to expend an incredibly high amount of effort to keep their interfaces up to date.
To this end, the following formula illustrates the complexity for a general-purpose user provisioning tool:
QS: Source system
If: Interface
n: n. system
ZS: Target system
V: Versions
If(QS) *No(QS V) * If(ZS 1) * V(ZS 1) * If(ZS 2) * V(ZS 2) * … * If(ZS n) * No(ZS1 n)
In fact, manufacturers try to find a way in between so that many systems can be easily provisioned and offer connectors for this purpose. This suggests that integrations are easy, but in practice they are not so easy due to the combinatorics (enumeration) described above.
As a rule, user provisioning in companies is a challenge, the implementation of which usually causes a lot of effort. This is not least due to the fact that systems do not meet the standard of the technology, on the part of the target systems but also on the part of the IAM(s).
Modern user provisioning
An advanced IAM has suitable interfaces that trigger user provisioning based on events, such as when a user receives a new authorization. This allows automatic processes to be triggered which then perform the provisioning. To do this, these workflows can themselves retrieve or update information via the IAM’s APIs.
Even if companies have a variety of software solutions, the question arises as to how many of the systems really need to be provisioned with user information or whether the information in the tokens is perhaps ideally sufficient.
The user provisioning processes are usually not particularly complex, regardless of this, they can either be implemented with simple scripting languages or you could use a low-code/no-code platform (iPaas).
The advantages:
- Less provisioning.
- Real-time provisioning.
- Ability to implement different workflows depending on selected permissions.
- Overall, less effort to implement and support user provisioning.
Authentication and authorization management newly conceived
Authentication for more security and access control
Passwordless authentication methods have become standard, but if an IAM does not offer at least 10 different methods, it becomes difficult to perform multi-factor authentication and step-up authentication in a reasonable way. An IAM should control access to an application by checking the corresponding entitlements after authentication. It is even more important that an IAM is aware of all applications and that an application is not just information or a proprietary object within the company.
Authorization management
Authorization management is more than just assigning or removing a user’s entitlements. In particular, analyzing the effective use of applications and authorizations simplifies processes such as recertification and also allows policy-based access control.
While the recertification process addresses the control and, if necessary, removal of authorizations, a process for ordering roles/authorizations is often implemented, whereby users can request authorizations for themselves or for colleagues.
For this purpose, we can differentiate at least two authorization requests:
- Access to a function: this is often paired with the corresponding roles that can be used to execute the function in an application system. Generally, there are several implementations of this in practice:
- The IAM checks whether access to the application is possible with the given permissions and the application itself uses these permissions for further user control – Ex: ERP system.
- The IAM checks whether access to the application is possible with the given permissions and the application controls and manages the permissions in the application independently – e.g., collaboration platforms.
- Access to an object: this form of access control makes sense, but it requires that the object resources are known to the IAM and that the IAM can control access to them. If we think of old generation file directories, this was possible by knowing them with exactly one known IAM. Modern file or directory shares today through services in the cloud that use the information of the user token for this, which uses the permissions and user information for this, which corresponds to point 2 in “Access to a function”.
With an advanced IAM:
- Ordering processes should be able to be implemented flexibly because.
- Application definitions and the defined authorizations can be retrieved via API,
- Users can be assigned or revoked appropriate permissions via API.
- If user changes can be tracked indefinitely in corresponding audit logs.
- Only relevant user and user permissions should be transmitted to the application.
- Extended access checks by re-authentication – step-up should be possible to confirm an authorization.
- The effective use of authorizations by a user should be tracked, the comparison of assigned authorizations to the used authorizations on the one hand and a possibly desired verification of a segregation of duties on the other hand be easily possible.
- Regular exports of all users in a batch process should not be necessary, because the IAM informs about every change at a user and just in case of changes. This has several advantages:
- changes become known promptly
- this approach works well even with a large user base,
- the process is much more efficient in terms of energy, so that the path to Green IT can be pursued consistently.
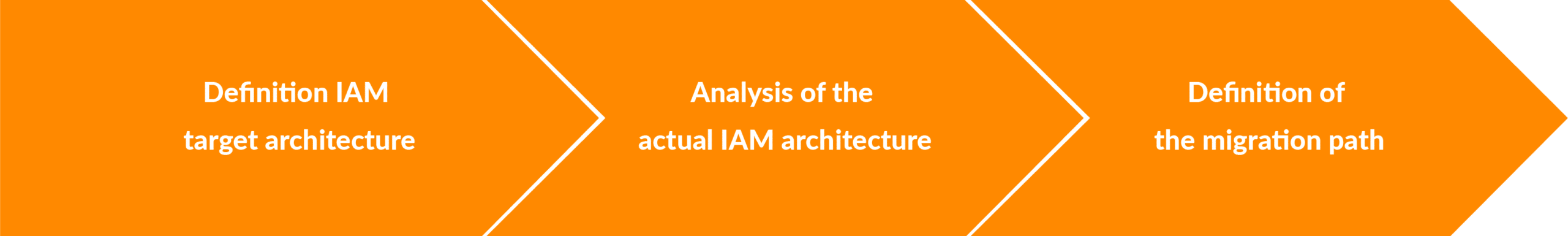
The way to a new Workforce IAM solution
The following top-level process may look trivial, but in fact you should start with the target architecture. The best results can be achieved quite quickly with the target image, because many key points are basically specified by standards and which further requirements are needed can be derived, for example, on the basis of the security specifications. The requirement for multi-factor authentication is of course mandatory.
The survey of the as-is architecture may require a thorough analysis, but the main point is that this result can be used to derive various areas that can be included in an iteration when defining the migration path.
If possible, the migration should be implemented in steps. This makes the entire introduction manageable, and the migration path should also definitely outline a time schedule so that the migration progress can also be monitored. Unfortunately, migrations are also dependent on external prerequisites or results, so the migration path should also always provide for alternative sequences.
The migration steps should be taken in such a way that more applications continuously use the target IAM and, consequently, the obsolete solutions become less and less important.
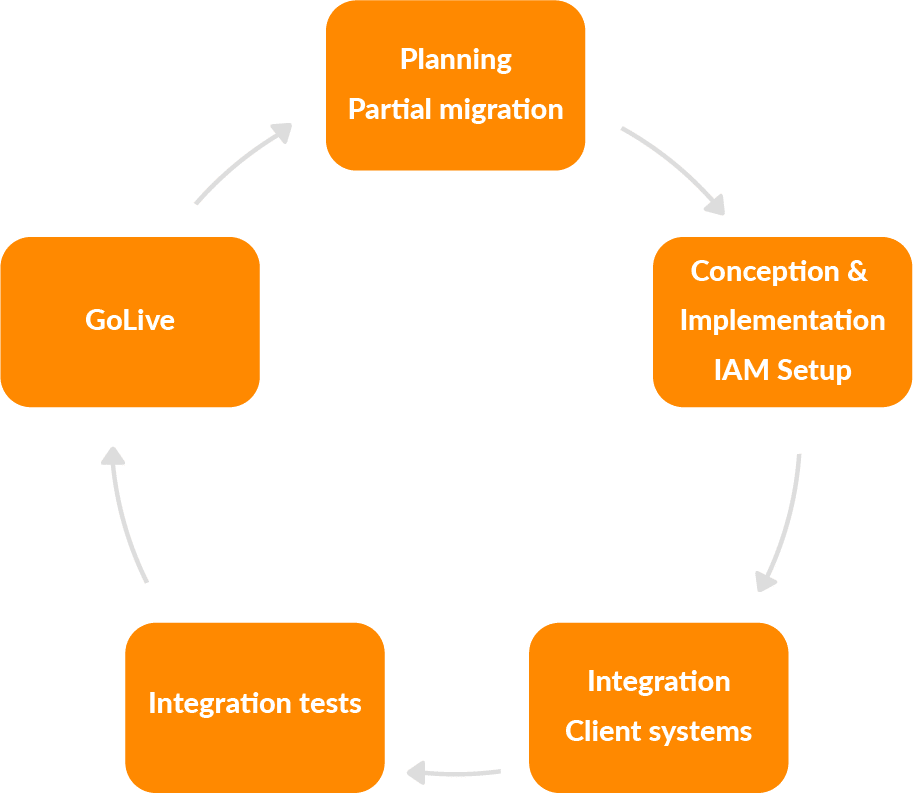
The following points can be helpful for the implementation of the target IAM:
- Determine that new software solutions will only be implemented if they comply with the standards of the target IAM and preferably support the OIDC/OAuth2 protocol or at least SAML2 protocol.
- Define a roadmap in which order you want to integrate IAM into your existing applications. Start in areas that are subject to major changes anyway due to your digitization strategy and plan these changes with the new IAM.
- Choose a target IAM that can act as an identity hub and where it is possible to integrate your old IDP, so that the majority of users can already use the target IAM.
Conclusion
By implementing an IAM, organizations can not only protect their digital assets, but also ensure compliance with data protection regulations. With an IAM system, organizations can manage user identities and control access to resources while ensuring a seamless user experience. This not only enables more secure operations, but also increased agility in an ever-changing business environment.
The use of an advanced IAM is essential in this regard, otherwise new applications are difficult to integrate. The target IAM architecture should be defined with the highest priority.
There are certainly many aspects that are important when selecting an IAM solution, but a few basic points should simplify the decision:
- An IAM platform should be consistently based on standards; these standards are essential for easy, sustainable use, as well as acceptance in the company.
- The IAM platform should have comprehensive, secure web APIs and implement an event-driven architecture, making integration with all solutions in the company and also for third parties much easier.
- One can expect active security measures from an Identity & Access Management, such as fraud detection and prevention, as well as security dashboards.
- An IAM must have an excellent UX because users will use the IAM regularly and adoption will quickly fade if this is not provided.
- User provisioning should be done with moderation and purpose, basically:
- Better to share user information with the application at the time of use because it is maximally up to date, as well as the transfer is secure and standardized as part of authentication – so do not provision.
- An IAM is not good just because it has “the most connectors”, mostly because individual adaptations are necessary or the connectors cannot be used in the context and many connectors are not needed at all, but some are not in the repertoire.
- With no-code/low-code platforms or integration scripts, provisioning can usually be implemented better and more accurately.
- Differentiation between IAM and identity governance (analysis, recertification, modeling, possibly also ordering processes) is the right way. APIs can usually be used to create a simple connection. An IAM should have the appropriate functions, but in reality there may already be other ways of ordering, for example, and the ordering of authorizations is only a partial step. Also, the modeling of roles and the definition of the required authorizations can be done elsewhere as part of process analysis.
- For several reasons, it is recommended to use a SaaS solution as the target IAM:
- It saves a lot of time, effort and costs during setup as well as especially during operation.
- The application area of workforce IAM radiates long beyond the own physical locations, is used by employees mobile, also more and more applications are also cloud solutions.
- Advanced IAM platforms are constantly updated, even during operation, so that no measures need to be planned in the company with regard to the security and up-to-dateness of the solution.
Additional functions complete the repertoire of the IAM platform. With the leading Identity & Access Management from cidaas, you get a future-proof IAM that also offers other very good features such as consent management. This allows to request digital consents for internal or external employees e.g. for data protection regulations or data processing purposes at login.
The cidaas ID validator offers a highly secure and efficient online identity verification using artificial intelligence and machine learning. It identifies a person with ID document and facial matching according to the eIDAS regulation, thanks to AutoIdent fully automated and without interaction with another person. This allows new employees and partners to be onboarded without having to come to the company headquarters. It can also be used to grant access to highly secure applications.
Don’t miss our first part of the blog series “Workforce IAM – the evolution which is a revolution”:
