Identity theft: The 3 most common hacker attacks
Every company now has digital identities through the bank. In one case, it is more like employee data, in another, it is countless customer data. We owe this to digitalization and the new possibilities in the form of digital services. This also increased the potential for hacker attacks.
As a rule, users gain access to the digital service by entering a username, an e-mail address, and the password they have been given.
In some cases, passwords must also be changed after a certain period of time and set according to certain password rules, so that they are as complex as possible.
Are passwords and password rules the ideal protection?
I think the answer to this question is quite clear. But passwords are not insecure per se. Rather, we make them insecure because we often reuse them or create them so that we can still remember them.
In early February, the BSI took leave of the following item on security and passwords: “Passwords should contain upper- and lower-case letters, numbers and special characters and should be changed periodically.”
Which hacker attacks are there and why do password rules not help?
Phishing:
Let us unpack the dictionary definition. “Phishing means the interception of data from Internet users via fake Internet addresses, e-mails or SMS.” (Gabler Business Dictionary)
Basically, it is exactly that, criminals try to trick users into entering their access data via e-mails, SMS or other media, some of which appear very authentic.
In this context, I would like to mention the term social engineering attack. The users are manipulated by interactions and abilities of the attacker and are therefore unfortunately a risk. For this reason, security awareness training courses are typically held in companies, in which exactly these types of dangers are pointed out.
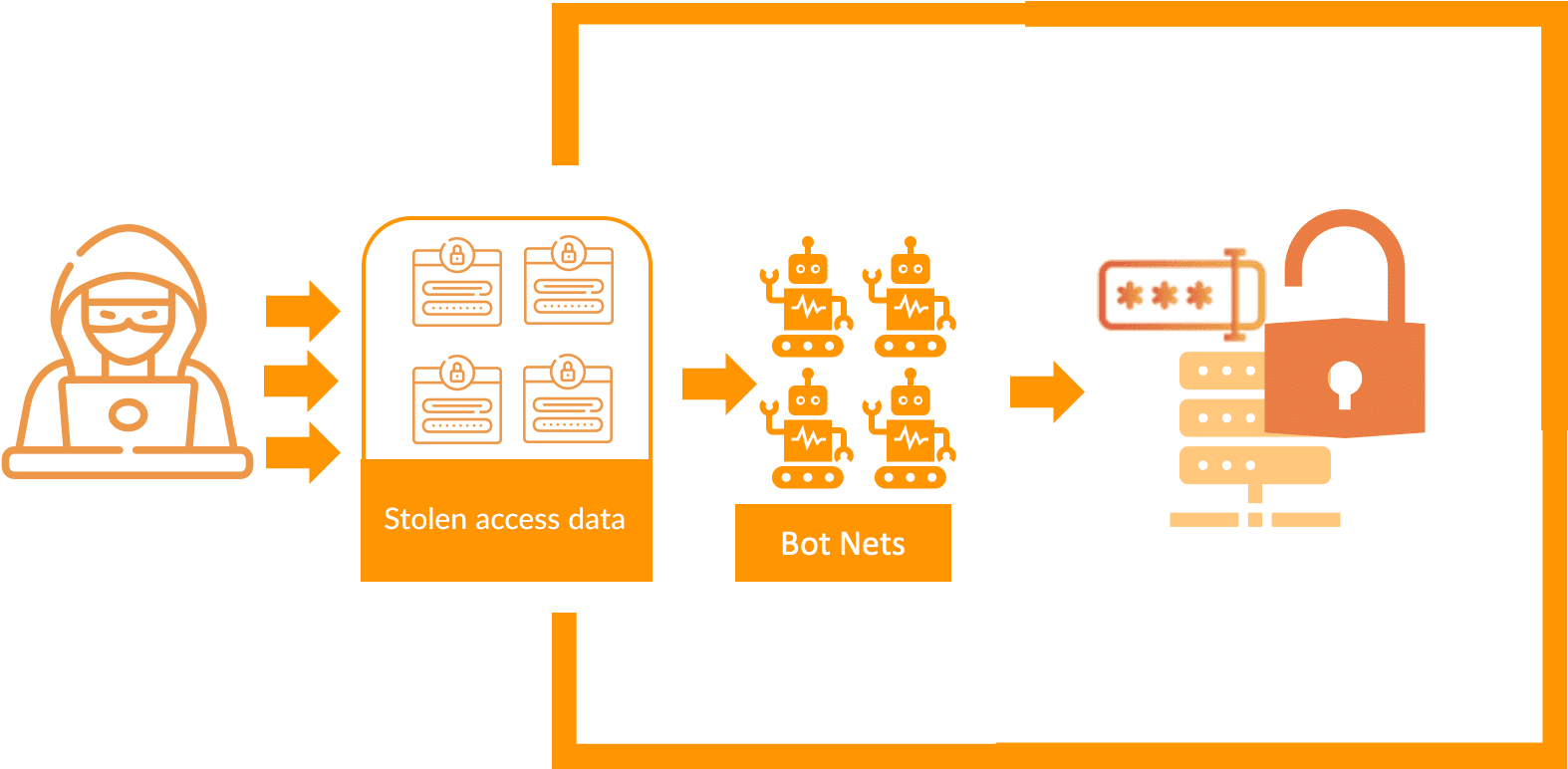
The access data can quickly fall into the wrong hands and a password rule has no protection mechanism at all.
Password Spray / Brute Force:
In password spray or brute force attacks, the most common passwords are used and tried on countless accounts. This is a way to bypass the number of attempts before the next common password is tried.
Brute force means that login attempts are made by a machine within a very short time.
Password rules can even have negative effects. As soon as it is known which password rules are used, some common passwords can already be excluded. As a rule, they provide at least a little protection, as this typically makes users’ passwords more complex.
In principle, however, the protection here is not sufficient. Instead, the value should be placed on smart multi-factor authentication and botnet detection to counteract such attacks.
Credential stuffing
Data theft and the sale of data on the Internet seems to be a lucrative business. Since users like to use the same login data on different platforms, Credential Stuffing has emerged as a new form of brute force attack.
Well, you cannot really blame users for it either. There are so many digital channels, platforms, and services and different devices on which you want to use all these services. A user simply cannot remember passwords in this number.
The stolen access data is therefore tried out on the various platforms during credential stuffing to gain access to the user account.
In our opinion, there are two important measures to be taken against this: Again, Bot Net Detection is critical to detect and block a bot network. Second, for users, password-less methods, such as those we already use on TouchID smartphones, or one-time passwords, offer not only greater convenience but also much greater security and protection against identity theft.
If you want to know more about security, check out our article “Security for data in the digital and real-world” or see how our customers use cidaas.
