Digital identity verification
AutoIdent by cidaas ID validator
Online identity verification using artificial intelligence and machine learning.

Businesses which already rely on
cidaas ID validator



What our customers say about the cidaas ID validator
Stephan R. Peters
Technical Lead Smart Districts, Schwarz IT KG – Bildungscampus Heilbronn
ID Verification made easy with the AutoIdent by cidaas ID validator
01
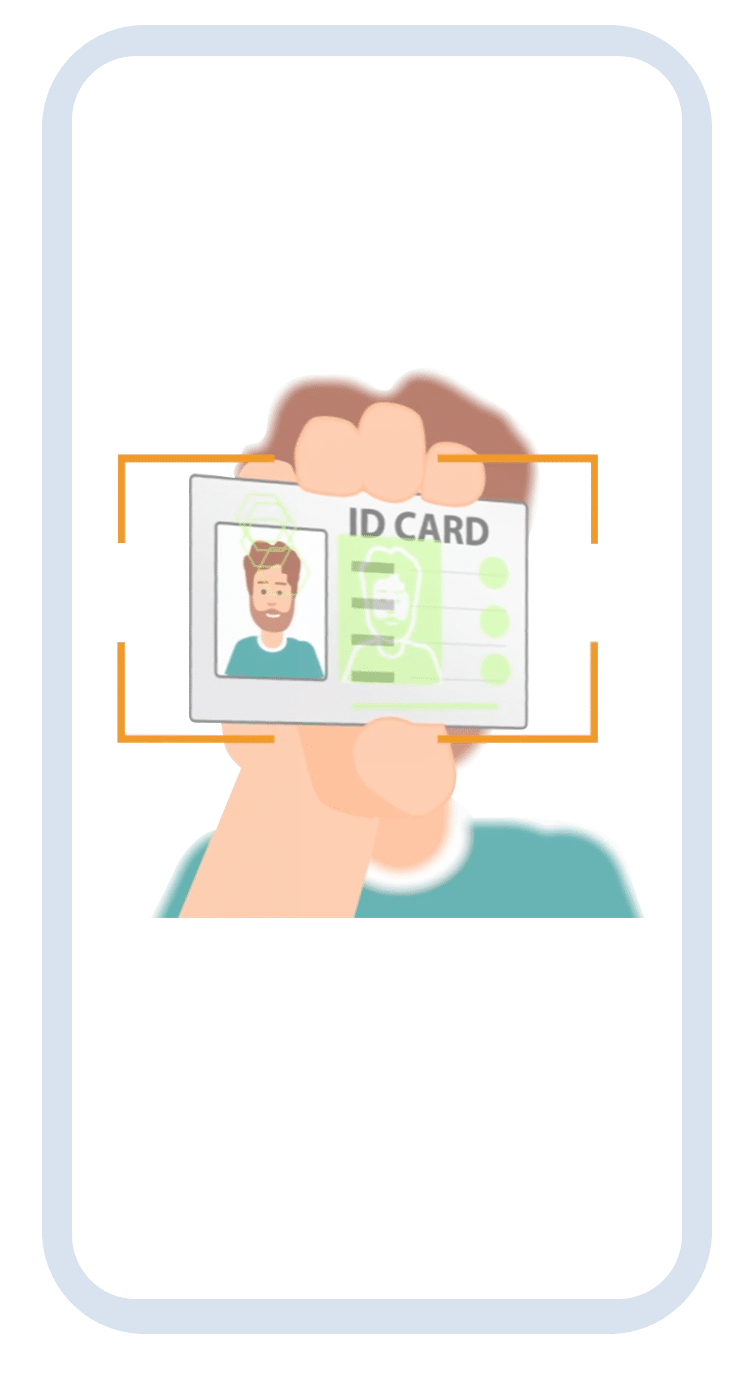
1. Validation of the ID document
In the first step, the ID document is scanned and validated. The system first automatically recognizes the type of ID card and checks its authenticity using specific security features. For this purpose, personal and biometric data is also extracted for comparison with the face scan data and the authenticity of the document is checked.
02
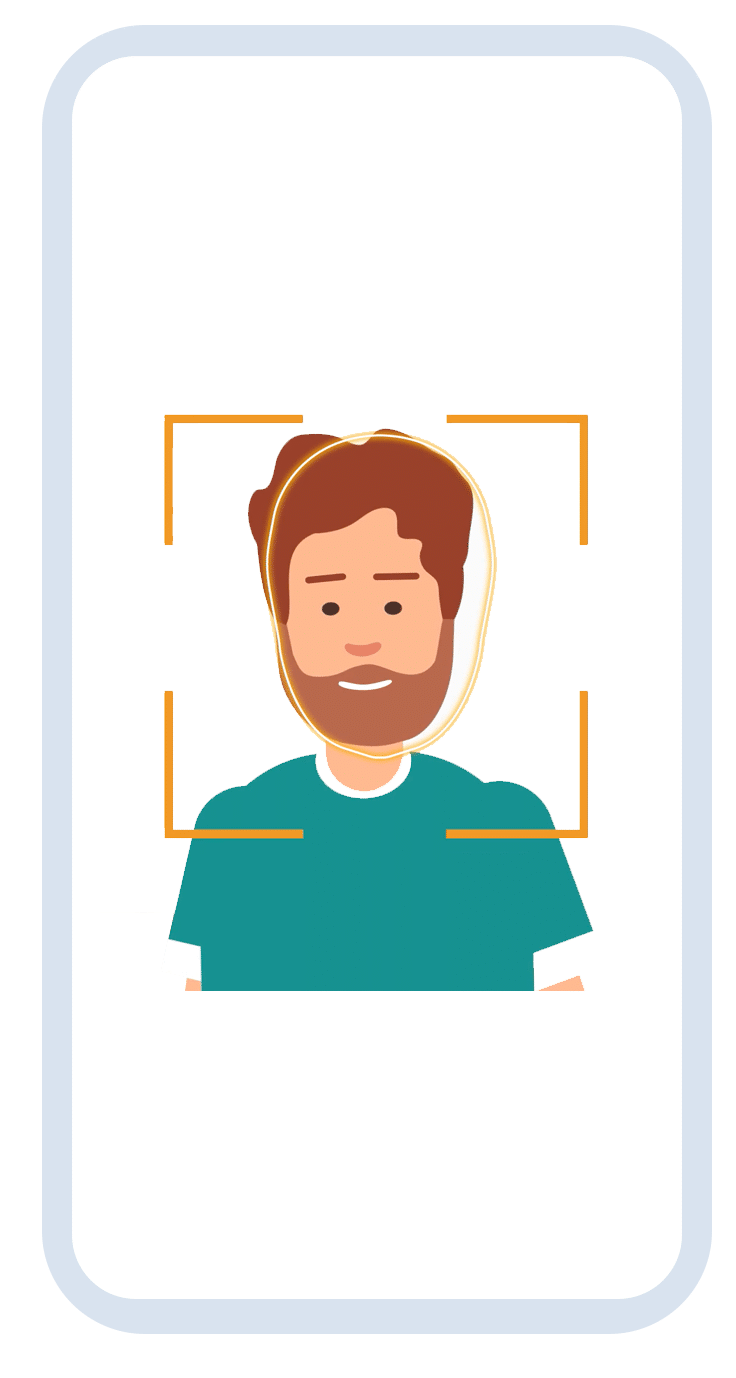
2. Face scan
In the second step, the face is scanned and a person’s authenticity is verified. The artificial intelligence scans precise biometric facial data and extracts it to perform a digital identity check. In addition, the realness of a person is verified using randomized movements.
03
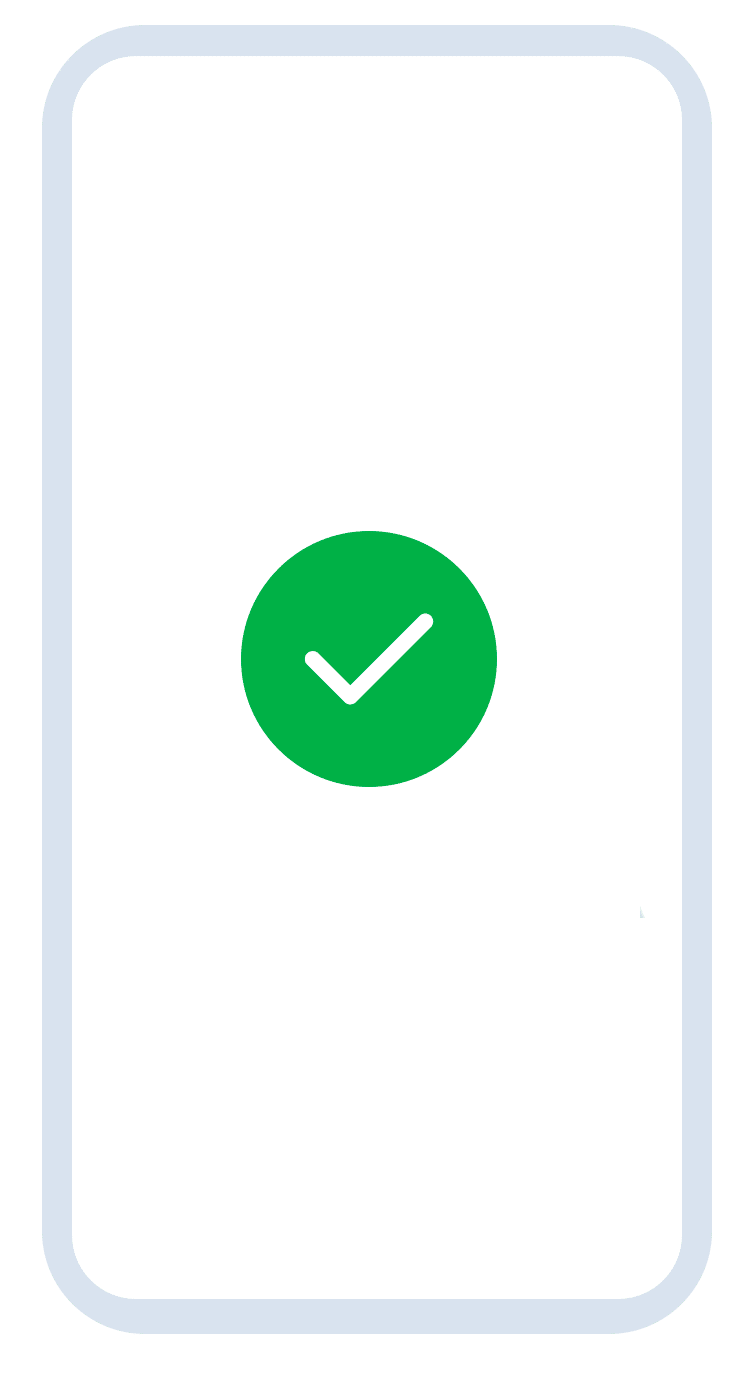
3. Intelligent analysis using AI
Immediately after the facial scan, an intelligent comparison of the extracted biometric data of the face and the ID card image takes place with the help of artificial intelligence. This confirms the identity of the user. In addition, a data consistency check is carried out between the front and back of the ID card.
Digital contracts
Driving license check
Age verification
Onboarding
ID Verification – anywhere and anytime!
Identity verification is needed for a wide variety of use cases, from age verification when purchasing alcohol to driver’s license verification to identity verification while opening an account. The cidaas ID validator is a verification solution which allows to verify different identity documents in real time. We rely on an AutoIdent, a fully automated video-based legitimation, which guides users through the verification of their identity without any interaction with an agent. In addition to a significantly more efficient cost structure, this has a major impact on the customer journey and ensures the best customer experience. After all, who wants to talk to an agent on the couch in the evening? The cidaas ID validator not only convinces with highest security, but is also eIDAS compliant.
cidaas ID validator for increased security
The cidaas ID validator not only impresses with its user-friendliness and ease of use, but also meets the highest security standards and is GDPR-compliant and eIDAS-certified.
Real-time
Real-time processing
Verification that processing is in real-time and not recorded.
Improve Security
Deep Fake Detection
Detect Deep Fakes and manipulation of video or documents.
Perfectly integrated
Part of the cidaas platform
Utilize the perfect integration into the leading European CIAM – cidaas.
cidaas ID validator is integral part of Schufa MyConnect Hub
With MyConnect Hub, Schufa has created a unified service for the digital sales process and onboarding in regulated areas. The cidaas ID validator is an integral part of the MyConnect Hub, enabling the verification of identities based on an AutoIdent and thus the first step in the customer journey. In this way, digital contracting such as the conclusion of a loan agreement is easily and completely digitally mapped.
- eIDAS compliant ID verification for regulated use cases
- Integrated with a Qualified Electronic Signature (QES)
- Fully digital and fully automated

Frequently Asked Questions
What you ever wanted to know about digital identity verification with an AutoIdent!
What is AutoIdent?
An AutoIdent is an innovative and fully automated digital identity verification. The video-based process the id document and the face of the user are scanned and with the help of AI technologies verified. Thereby numerous security checks, like liveness detection or id card verification are conducted, to ensure highest security as well as an accurate identity verification.
What is a Liveness Detection?
A Liveness Detection is a technology that is utilized to verify that the AutoIdent process is performed by a real human being and no photos or videos are used to manipulate the identity verification.
For what use cases do I need an Identity Verification?
Identity verification is useful for many use cases. Besides obvious use cases in the highly regulated area, such as opening a bank account or a loan, less regulated use cases such as a driver’s license check or age verification are also interesting. Often, identity verification is also utilized in the context of onboarding, e.g. remote employees or students during enrollment, to increase the assurance of users.
Why do you need an AutoIdent?
An AutoIdent delivers many benefits to both the businesses that implement it and the users that need to perform it. Firstly, the costs of an AutoIdent-based approach are many times lower than those of VideoIdent or PostIdent-based approaches. On the other hand, it offers a much better customer experience. This results in particular from the shorter processing time of an AutoIdent, and moreover it is an automated process without interaction with an agent. Finally, the video-based approach of AutoIdent makes it possible to verify a wide variety of identity documents.


Pick the plan that's best for you.
Grow faster with us!
Get in touch with us now or take a look at our Identity verification options!
Card Validation, Ident Validation or Legal Validation the right solution for every use case.
1,50 €
Card Validation
- Automated ID card check
- Badge recognition
- ID document check
2,50 €
Ident Validation
- Automated digital identity verification
- Face recognition and matching
- Liveness Detection
4,50 €
Legal Validation
- Real-time audit
- Fraud detection
- eIDAS compliant

