Goodbye SAP IDM: End of Life – Time to Rethink Identity Management
The SAP IDM End of Life: What’s Happening when?
SAP IDM, the long-standing identity lifecycle platform used to provision and manage access in SAP-heavy landscapes, will no longer be supported. The mainstream maintenance officially ends in 2027 .
SAP will not offer a direct successor.
Instead, they have partnered with Microsoft to promote Microsoft Entra ID as the suggested target platform. A move that signals a shift toward cloud, but also introduces new challenges around vendor lock-in, operational complexity, and data sovereignty.
A Strategic Inflection Point
Many enterprises, especially in retail, franchise, logistics, or manufacturing, have historically relied on SAP IDM not only for user provisioning, but also as a lightweight IGA solution for other apps, Active Directory, and decentralized roles.
As a result, replacing SAP IDM isn’t just a technical migration — it’s an architectural redesign with long-term implications:
| What SAP IDM was used for | Replacement Consideration |
| SAP user provisioning (HCM/SF) | SCIM / SAP CIS + Entra / alt. |
| Role mapping & SoD prep | IAG / GRG / SaaS-based governance |
| NetWeaver / SAP Portal auth | SAML / OIDC via modern IdPs |
| Workforce lifecycle management | Entra ID Governance / iPaaS |
| Manual UI flows / self-service | Custom workflows or low-code |
And here’s the crux: Most of those tasks can now be covered using open standards without committing to a monolithic suite with complex migration paths.
SAP IDM End of life, Enter: Open Standards & Sovereign SaaS
The modern IAM landscape is vastly more interoperable than it was a decade ago. Thanks to SCIM, SAML, OIDC, and REST APIs, identity platforms can now integrate with HR systems, SaaS apps and environments, and internal portals without needing everything from a single vendor.
This is where cidaas, a European Identity-as-a-Service provider, enters the picture:
- Built on OAuth2, OIDC, SAML, SCIM and REST
- Delivered as a multi-tenant or private cloud SaaS
- Hosted in Germany or Switzerland
- Certified to ISO 27001, GDPR-compliant by design
- Supports delegated group management, self-service portals, and API-first integration
Unlike Entra ID, which is tightly woven into Microsoft’s enterprise fabric, cidaas is vendor-neutral and open for integration in mixed environments (SAP, Microsoft, legacy, custom and other).
Modular Identity Architecture Instead of Monoliths
With the end of SAP IDM, organizations have the chance to shift to a modular IAM stack, for instance:
- cidaas as the central identity solution for workforce (employees) and B2B (partner)
- cnips (iPaaS) for workflow orchestration and data mapping
- SAP Cloud Identity Services as SCIM/SAML integration target
- SAP IAG (if needed) for deep SoD analysis and SAP-specific governance
- ServiceNow or Portal for user self-service and request management
This modular approach ensures the following benefits:
- Lower vendor lock-in
- Better alignment with internal responsibilities (HR, IT, Security)
- Faster time to value
- Digital sovereignty and data control
SAP IDM End of Life and the Need for Re-Architecture
With the sunset of SAP IDM approaching, many organizations are asking themselves a critical question:
“What’s the right architecture for identity and access management, not just for today, but for the next decade?”
Here´s How to Prepare for the SAP IDM End of Life:
For companies with SAP-centric landscapes, complex identity flows, and hybrid environments spanning employees, partners, contractors, and other applications, the answer is rarely a simple drop-in replacement.
SAP IDM has long been the glue for user provisioning and access control across SAP and other systems. But with them officially ending IDM support by 2027 and no successor in sight, a new strategy is required.
Most enterprise IAM landscapes today are far more complex than a decade ago and crucial requirements include:
- HR systems like SAP SuccessFactors drive identity creation
- Applications are hybrid: Cloud, on-premises, mobile, legacy
- Users include not just employees, but partners, service providers, and externals
- Compliance, auditability, and data sovereignty are top concerns
- There’s a growing demand for decentralized workflows and faster onboarding
Rather than re-creating the same complexity with a software solution, this is an opportunity to modernize and simplify.
A Blueprint for a Standards-Based IAM
At the core of the proposed architecture are two key components:
- cidaas: A cloud-native identity and access management platform based entirely on standards (OIDC, SAML, SCIM, OAuth2).
- cnips: A low-code integration and automation platform (iPaaS) that acts as the orchestration layer between systems.
Together, they form a powerful and flexible stack that integrates seamlessly with SAP ecosystems – as well as other applications – without vendor lock-in.
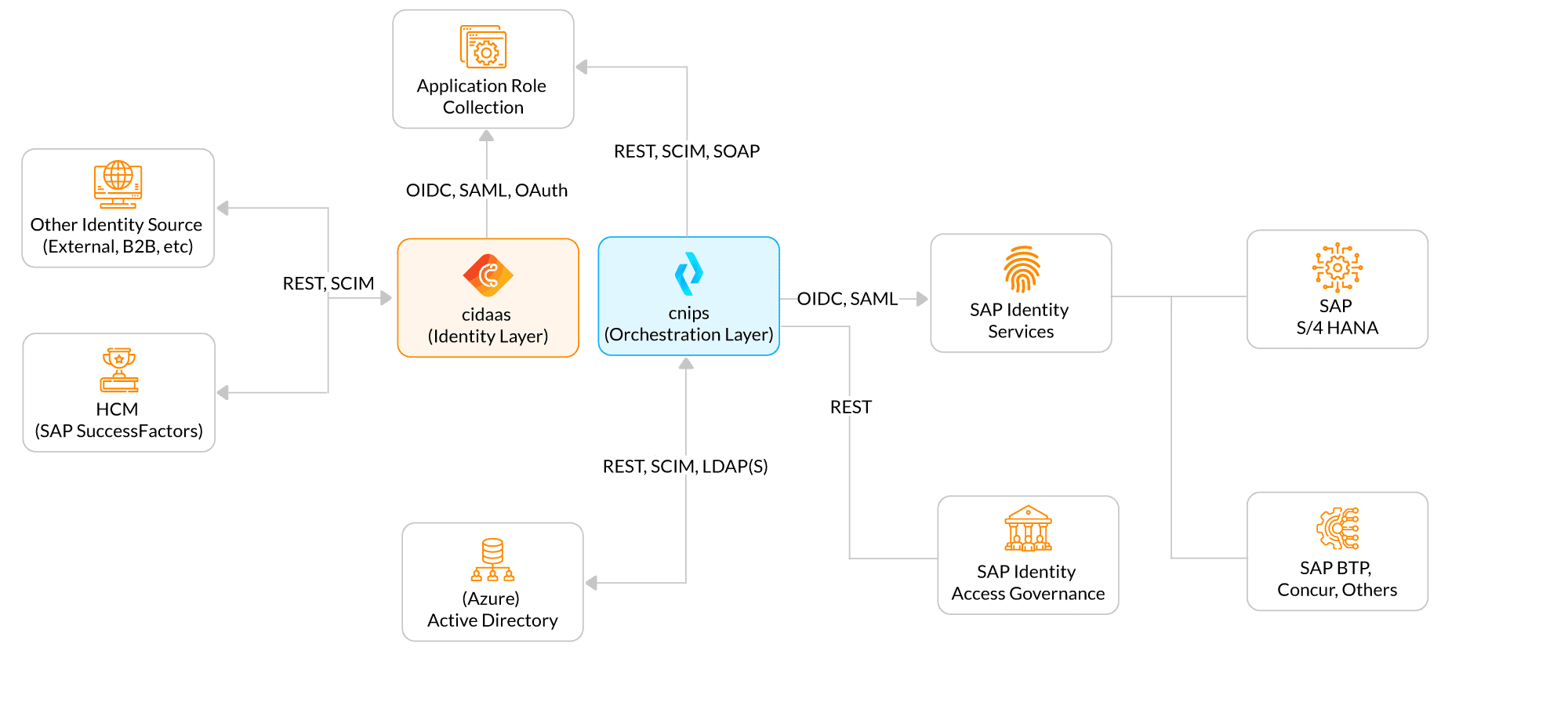
The Architecture: Modular, Extensible, Interoperable
Here’s how the pieces fit together:
- cidaas acts as the central IAM platform. Handling authentication, token issuance, MFA, and role & group management.
- cnips orchestrates identity flows, access requests, approvals, and provisioning across SAP, Active Directory, external applications, and beyond.
- Systems like Cloud Identity Services, S/4HANA, and SAP Identity Access Governance (IAG) are integrated via SCIM, REST, and SAML.
This architecture decouples concerns: Identity services are separated from process orchestration, and compliance tools can be layered as needed.
Identity Lifecycle & Authentication Flows
Let’s go one step deeper and look into the details:
1. Inbound Identity Management
Identities are sourced from:
- HR systems (e.g. SAP SuccessFactors, Workday, Personio, etc.) via SCIM or REST
- External sources (B2B portals, delegated onboarding, project-based access)
These users are provisioned into cidaas, enriched with metadata (e.g. roles, departments, legal entities), and prepared for downstream provisioning.
2. cidaas as Identity Provider
cidaas supports authentication via:
- OIDC, OAuth2 and SAML 2.0 for cloud and enterprise applications
- MFA policies, including biometrics, OTP, and device context
- Custom-branded login pages and self-service portals for different user groups
cidaas also supports delegated group management, allowing business owners or team leads to manage memberships without burdening IT.
3. Orchestration via cnips
Once users exist in cidaas, cnips triggers and manages:
- Lifecycle workflows (joiner, mover, leaver)
- Multi-step approvals for access requests
- Attribute transformation and mapping (e.g. org codes, country-specific roles)
- System-specific field normalization
- Integration with ITSM systems like ServiceNow
This orchestration engine ensures processes are transparent, auditable, and adjustable without writing code.
4. Downstream Provisioning
cnips provisions users via SCIM, REST, or even SOAP to:
- SAP Cloud Identity Services (CIS) and S/4HANA
- SAP IAG for access governance and risk analysis
- Active Directory / Azure AD
- Other applications and SaaS systems
Where advanced SoD, attestation, or recertification is required, cnips can either:
- Integrate with SAP IAG for SAP-specific access governance
- Drive external processes via its workflow engine or third-party GRC tools
Why This Architecture Works
This standards-based approach has already been adopted in complex enterprise environments – not just because it replaces IDM, but because it improves on it.
Key benefits include:
- Open standards: SCIM, SAML, OIDC, REST are future-proof and interoperable.
- Vendor-neutral: cidaas and cnips are not tied to Microsoft or SAP licensing models.
- Cloud-native: Available as SaaS or private cloud, scalable and always up-to-date.
- Sovereign hosting: Fully GDPR-compliant, with hosting in Germany/EU or Switzerland.
- Decentralized workflows: Business users can take responsibility for access, reducing IT overhead.
- Low-code automation: Fast rollout of identity processes, adaptable to local requirements.
Don´t just replace SAP IDM with another “one-size-fits-all” tool. Go from legacy to lean. Replacing it is not just about matching features. It’s about rethinking the model entirely.
SAP IDM End of Life: Request, approve, assign with cidaas
How cidaas and cnips-iPaaS enable full-lifecycle access governance without the IGA bloat.
Modern access governance is caught in a paradox. On the one hand, organizations need fine-grained control over who can access what, especially in complex landscapes with business roles, data context, and compliance requirements.
On the other hand, traditional IGA platforms are often overkill: Monolithic, expensive, and difficult to adapt to real-world workflows. This is exactly where cidaas, paired with the cnips, iPaaS layer offers a modern, API-first alternative. Together, they enable not only self-service access requests, but also multi-step approval flows and automated role assignments – all while keeping the architecture lean, modular, and open.
Let’s walk through how it works.
From Request to Role Assignment – A Streamlined Governance Loop
In this architecture, cidaas acts as the central identity and role platform, while cnips orchestrates process logic, handles approvals, and connects to SAP business systems.
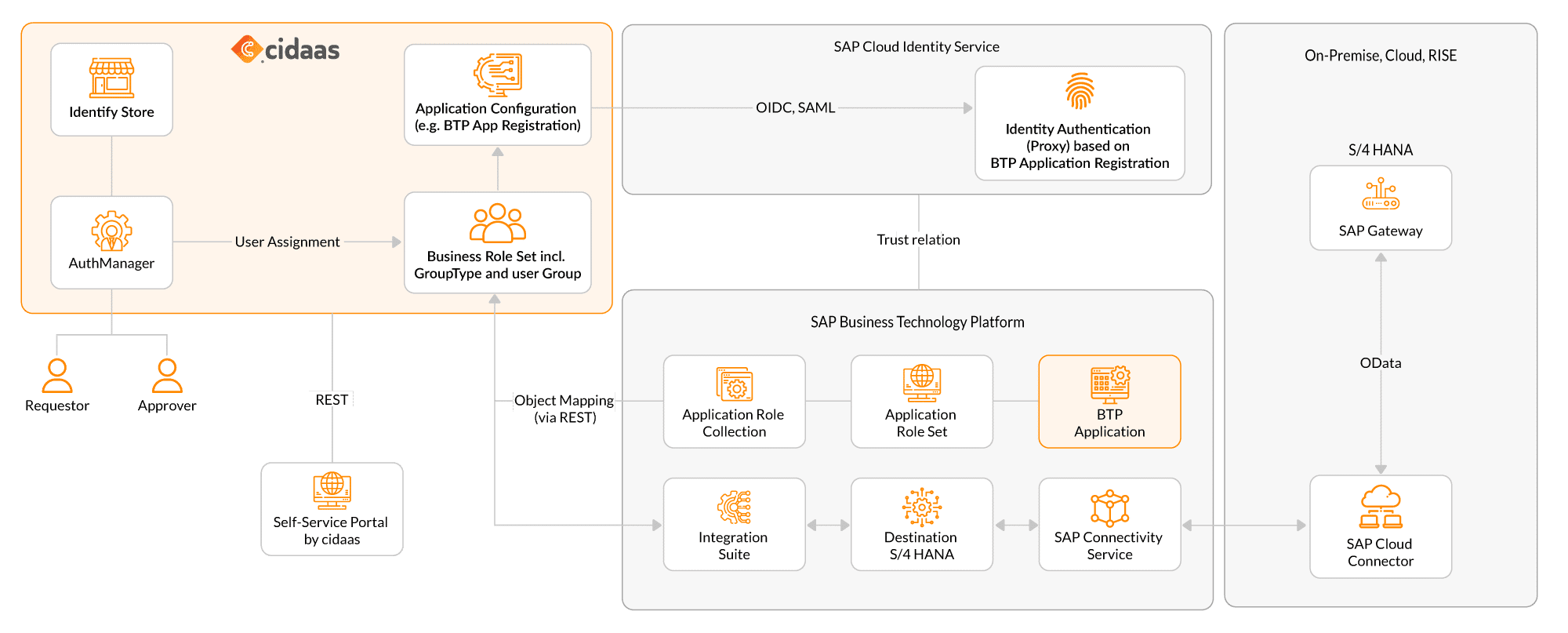
Here’s what happens step by step:
- A user (internal, partner, or external) accesses a cidaas-powered self-service portal.
- This request is handed over to cnips, which runs the approval and orchestration logic.
- Upon approval, cidaas updates the user’s business role assignment in the Identity Store, reflecting the granted access.
- The change is mapped to one or more Application Role Collections in SAP BTP or provisioned to SAP Identity Services via SCIM, REST or claim injection (OIDC/SAML).
- Optionally, cnips can call into SAP Integration Suite or SAP Gateway to validate context, apply business rules, or enrich requests with system-specific data (e.g., company code, plant, org unit).
Flexible Governance — Without the Overhead
Unlike legacy IGA systems, cidaas and cnips don’t force a predefined governance model. Instead, they allow organizations to implement just enough access governance, while retaining full control. Some key strengths of this approach:
Context-Aware Role Assignment
Roles in cidaas are linked to group types and business attributes. This enables context-specific access decisions, for example, only granting finance roles to users in certain regions or legal entities.
Seamless Approval Chains
cnips can model multi-step approvals based on org structure, project ownership, or other identity metadata. Approvals can be executed in Microsoft Teams, a web portal, or native enterprise systems.
Reversible & Auditable
Every access change is tracked, time-stamped, and can be reversed automatically. This ensures compliance with internal policies and external regulations – without the complexity of full-blown GRC stacks.
Integration-First
Since both cidaas and cnips are API-native, they integrate easily with ticketing systems (e.g., ServiceNow), business workflows, and SAP tools. There’s no “black box” logic or proprietary workflow engines.
Three Closing Thoughts on SAP IDM End of Life
The SAP IDM end of support without a designated (or explicit?) successor gives room for thought:
- Instead of migrating to a new “one-size-fits-all” tool, simplify your identity landscape: SaaS IAM is ready. Modern tools like cidaas now offer enterprise-grade IAM in the cloud — fast, scalable, API-first.
Open standards enable choice. SCIM and SAML let you plug into SAP or any third-party system. Retail and B2B models are changing. You need flexible onboarding, delegated management, and support for non-employees.
Data sovereignty matters. Especially in the EU, relying on hyperscalers can raise GDPR risks. A sovereign SaaS avoids this. Plus, you already need to migrate. Why not simplify instead of replicate legacy complexity? - Replacing SAP IDM is not just about matching features. It’s about rethinking the model entirely. With a layered architecture like this, you can: Centralize control without centralizing every system and avoid massive upfront projects by incrementally replacing legacy integrations.
- Choose the best-of-breed solution for each task: Identity, provisioning, orchestration and governance. Whether your environment is SAP-dominated or hybrid with Microsoft, Atlassian, Salesforce, or industry-specific apps. This modular approach works. Access governance doesn’t need to mean deploying a monolithic IGA suite. With cidaas and cnips, organizations get a lean, modular, and adaptable framework for managing access. This framework fits cloud-first architectures, hybrid SAP landscapes, and complex B2B environments alike.First and foremost, it’s a powerful solution for those who need:
-
- Workflow-driven access control
- Federated identity with policy-based mapping
- Lifecycle automation with context
- Governance without rigidity
SAP IDM end of life – do we need to panic now? No – it´s smooth sailing with the successful template from cidaas and cnips.
Are you interested in learning more about your options after SAP IDM? Get in touch with our cidaas experts or take advantage of our free demo, we´re happy to help you succeed!
