Automating identity provisioning for SAP S/4HANA with cidaas
How cidaas optimizes user lifecycle management through open standards.
Identity provisioning for user accounts in enterprise systems such as SAP S/4HANA has long been a complex, highly customized process. Traditional IDM solutions were often based on monolithic workflows, static user databases, and manual approvals across fragmented user interfaces. With the advent of cloud-first architectures, this model is no longer fit for purpose.In this article, we explore how cidaas, a modern, SaaS-based identity platform, enables seamless, standards-based user provisioning in S/4HANA via SAP Cloud Identity Services (CIS).
Combined with SCIM, REST APIs, and a clear separation of roles and orchestration logic, cidaas brings clarity and automation to a historically chaotic problem, thus creating an ideal solution for modern identity provisioning.
What does identity provisioning mean in the SAP context?
Identity provisioning describes the automated provisioning of user accounts, roles, and access rights in systems such as S/4HANA and BTP. The goal of this provisioning is end-to-end lifecycle management from creation to deactivation and deprovisioning, including auditing and compliance.
With cidaas, these processes can be controlled centrally, enabling companies to ensure consistent access to applications and target systems without rigid IDM monoliths.
The result of identity provisioning in the interaction between SAP and cidaas is lower costs, clear administration, and greater security.
From HR or request to S/4HANA user – end-to-end
In a typical enterprise scenario, users originate from systems such as SAP SuccessFactors or are created through delegated onboarding (e.g., partners, external users).
These identities must be provisioned in:
- SAP Cloud Identity Services as the central identity directory
- SAP BTP or directly in S/4HANA, depending on the provisioning
- Possibly across on-premise and cloud environments (e.g., RISE with SAP)
This is how cidaas handles this process:
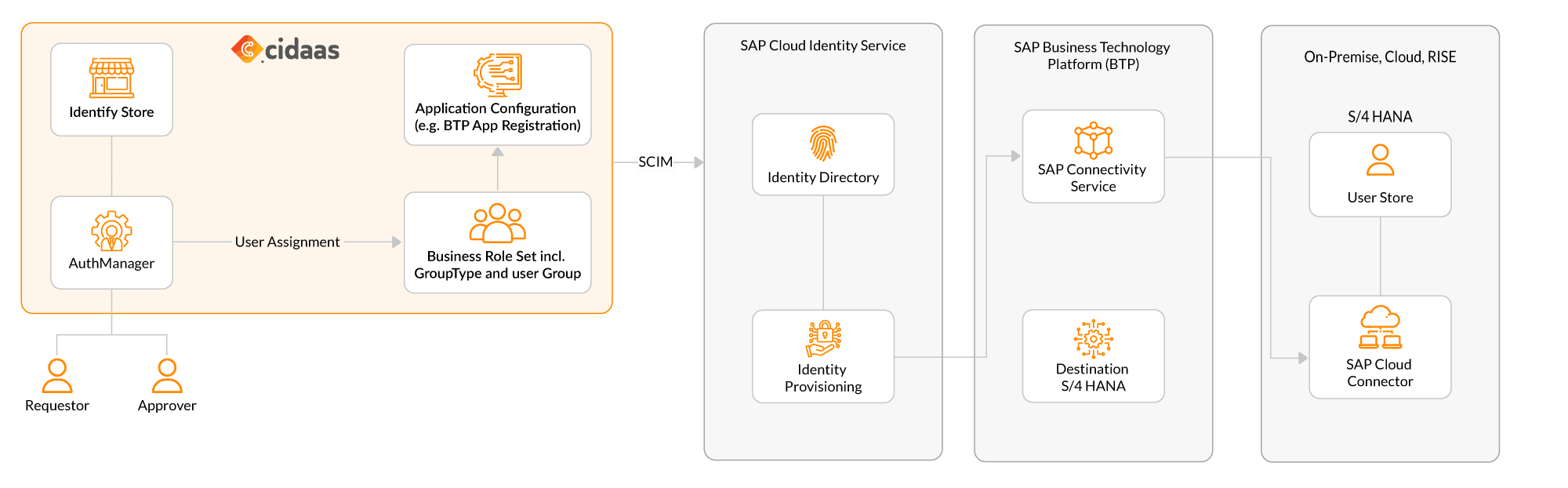
A closer look at the identity provisioning architecture
At the heart of the configuration is the cidaas Identity Store, which acts as the central layer for user and role management. Each identity is enriched with group assignments, business roles, and context-related attributes such as cost center, region, or department.
The cidaas AuthManager governs access policies and events in the user lifecycle: Onboarding, role changes, and deactivation. Assignments can be triggered either manually (via approval workflows), automatically (based on data sources), or externally (e.g., via SuccessFactors integration).
These identities are then forwarded to SAP Cloud Identity Services via the SCIM protocol, together with their group assignments. From there, SAP CIS takes over processing in downstream systems:
- Identity provisioning in SAP BTP
- Targeted access to S/4HANA via the SAP Connectivity Service
- Support for cloud and on-premise deployments via the SAP Cloud Connector
The entire process is modular, API-driven, and compliant with SAP’s reference architecture – and it comes with greater agility and adaptability.
IPS, IAS & cidaas – How integration works together
The SAP Identity Provisioning Service (IPS) synchronizes user objects and groups in connected target systems, while IAS (Identity Authentication Service) handles authentication.
cidaas fits into this architecture as a modern solution: Identity and access management with SCIM, REST, and a flexible directory. This creates a clear separation between provisioning, authentication, and management. This means that requirements from specialist areas and departments, from HR to IT security, can be implemented more quickly.
Process components in the lifecycle – from onboarding to deprovisioning
Effective identity provisioning covers all process components: Employee onboarding (creation), moves (role changes, department changes), changes (functions, authorizations) as well as deprovisioning (secure deactivation).
cidaas automates these steps based on rules, documents them for auditing, and consistently applies compliance policies. This keeps user accounts up to date, access rights minimal, and risks measurable.
Why SCIM is essential in identity provisioning
At the heart of this configuration is an important open standard: SCIM (System for Cross-Domain Identity Management). cidaas acts as an SCIM-compliant identity provider and enables:
- Standard-based provisioning in SAP CIS
- Easy, real-time identity synchronization
- Interoperability with other SCIM targets (e.g. SaaS tools, directories)
- Full auditability of provisioning operations
SCIM eliminates the need for custom connector logic, hard-coded interfaces, and SAP-specific user model translations. This allows organizations to focus on business logic rather than infrastructure.
Advantages of identity provisioning with cidaas at a glance
This identity provisioning model offers companies several strategic advantages:
1. Modular and open integration
By decoupling the provisioning logic from SAP-specific systems, cidaas offers a modular identity layer that works in both cloud and on-premise environments. This avoids hard dependencies on SAP IDM or proprietary tools.
2. Fast user lifecycle processes
New users can be created and assigned roles based on business rules, API triggers, or HR system integrations. Deactivations, role updates, and delegation processes are automated and event-driven.
3. Consistent policy enforcement
cidaas applies access rules and risk policies before provisioning even begins. Users who fail policy checks (e.g., SoD, regional restrictions) can be flagged, quarantined, or forwarded for manual review.
4. Audit-ready provisioning
All provisioning operations are logged in cidaas, with traceability down to individual fields and attributes. This facilitates the creation of compliance reports or the support of governance programs.
5. Future-proof access rights
Regardless of whether your landscape includes S/4HANA, BTP, or older NetWeaver systems, cidaas offers a future-proof solution for IDM without compromising on integration depth or compliance with standards.
Roles, permissions, and target system mapping in S/4HANA
With cidaas, permissions are modeled as business roles and transferred to S/4HANA and BTP artifacts via mapping. This allows user objects from the user store to be mapped to target systems in a targeted manner, including fine-grained access rights for applications. This reduces manual maintenance in the SAP backend and ensures traceable processes in management.
Security first – minimal rights and clean deprovisioning
Security depends on the lifecycle: Only those who perform a function receive the appropriate authorizations and automatically lose them when they change roles or leave the company. cidaas enforces least privilege, checks policies before assignment, and ensures timely deactivation in all target systems. This reduces the attack surface while keeping processes reliable.
Do I need IPS when using cidaas?
Yes, IPS remains central in the SAP target system. cidaas orchestrates identity management and delivers standards-compliant provisioning via SCIM – IPS distributed throughout the SAP world.
How do I prevent shadow access?
With a central directory, clear guidelines, and consistent auditing: Exchange is tracked, and access rights are automatically adjusted or revoked.
Final thoughts on identity provisioning
Provisioning users in SAP systems doesn’t have to be rigid, vulnerable, or slow. With cidaas and the SCIM integration model, companies get a powerful way to manage identity lifecycles. These are based on open standards, hosted securely in the EU, and designed for cloud-native and hybrid deployments.
Whether you want to replace SAP IDM or develop a new access strategy from scratch, cidaas gives you the flexibility and control you need to make identity provisioning a strength, not a burden.
Do you have any questions about what our product can do for you? Our experts are happy to answer them. Get in touch with us or book your free demo with us.
Don´t miss other blog posts from our IDM blog series:
Part1: Goodbye SAP IDM End of Life – Time to rethink identities
