
A Guide to Complete Zero Trust – Identity as the core building block of Zero Trust
In this final part of our blog on “A Guide to Complete Zero Trust’, we explore the role of identity as the core building block of Zero Trust implementation. For example, why Google is embracing identity with authentication and authorization as a core element of Zero Trust?
Although a new, promising model has been developed with emergence of Zero Trust, which can solve the problems of classic perimeter-based IT security concepts, the Zero Trust approach must also use certain parameters to decide whether access is permitted or not. Since the network is no longer a criterion, the focus shifts to the user and the accessing device. This makes identity the core building block of Zero Trust! The user and the device matter at two key points in Zero Trust implementation:
- During the checking of each access
- During the verification of access
User and device at access check
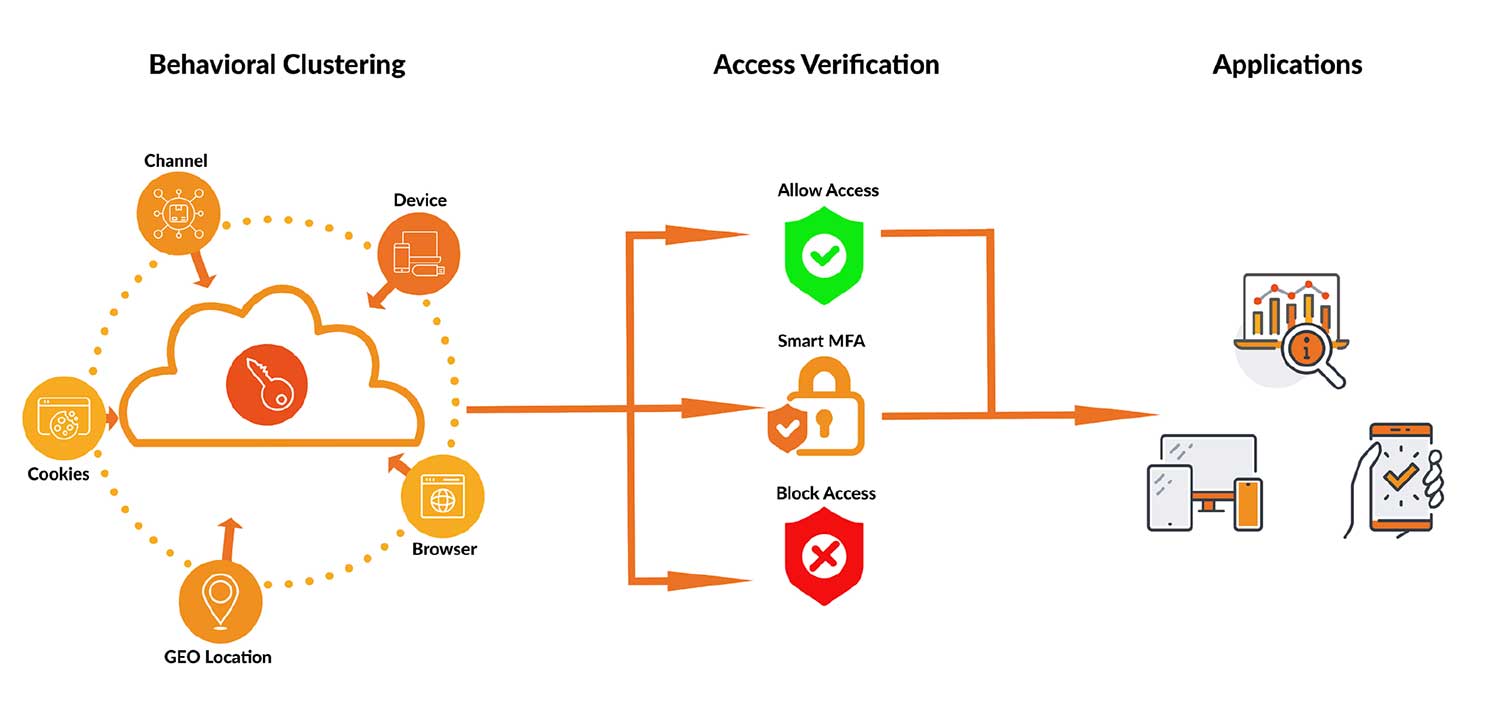
The motto of Zero Trust is “never trust, always verify”. This means that every access to a resource must be checked, and several signals are to be recorded and consequently evaluated. Signals can vary widely, but the most important signals include the resource being accessed itself, specifically the user and the device or its context. Google refers to these two categories as User Trust and Device Trust. The device trust collects a variety of information about the accessing device:
- Which device is being used?
- Which OS version is being used?
- How often was this device used for access?
- And a lot more.
Similar to device trust, user trust also records a variety of information about the accessing user:
- Which user is it and what permissions does the user have?
- Where is the user accessing from?
- Is the device assigned to or known to the accessing user?
- And a lot more.
The user and the device therefore serve as fundamental decision-making factors when verifying access. The access check can lead to three different results:
- Access is allowed
- Access is denied
- Further verification is required to allow access, for example multi-factor authentication
User and device at access verification
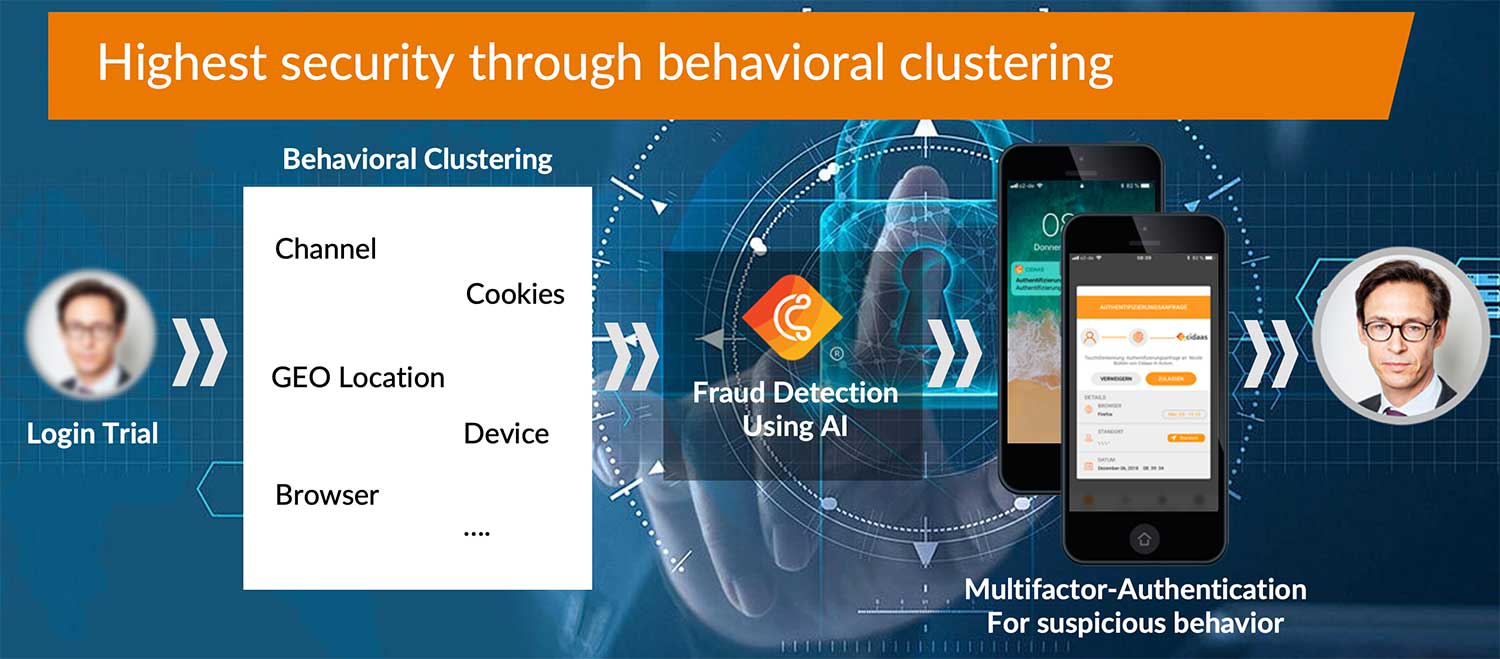
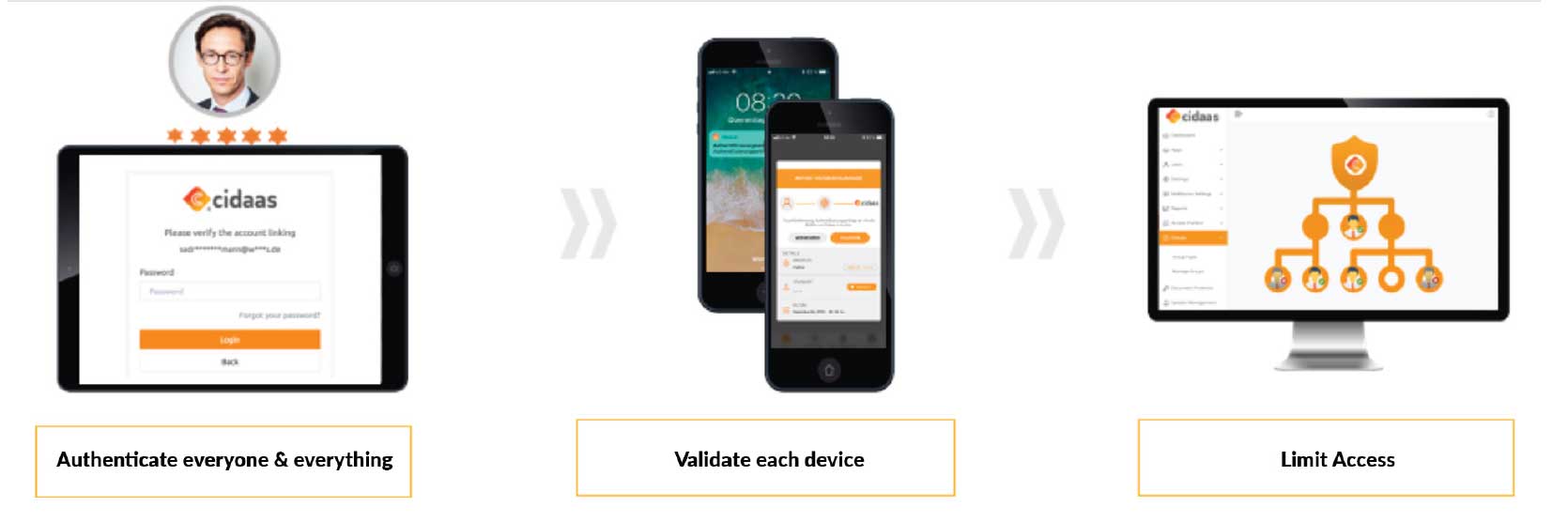
If the access check requires further verification, it is again the turn of the user and often also of the device. Multi-factor authentication can be used to confirm the identity of the user. In addition to the active authentication of the user, the stored device is often used as an additional factor. Besides SMS and e-mail, common multi-factor authentication methods include more innovative methods such as FIDO2, device biometrics such as TouchID or push-based methods.
A modern (Cloud) Identity & Access Management like cidaas is therefore the core component of an effective Zero Trust implementation, because Zero Trust is inconceivable without a user, device and authentication or verification.
cidaas Smart MFA and Zero Trust
The road to Zero Trust is long, because it is not only a significant change from an organizational point of view, but also a major transition from a technical point of view, in which the applications must be gradually transferred to the Zero Trust model. Besides the technical implementation, security must also be taken into account, because while Zero Trust is a good approach, it is the implementation in particular that determines success.
With the Smart MFA approach, cidaas offers adaptive multi-factor authentication that can be switched on based on risk. This way, the user and the device can be verified to confirm access, if necessary. In addition, the cidaas Smart MFA offers behavior-based clustering, which evaluates a wide range of signals when logging in and, if necessary, requests risk-based multi-factor authentication.
Don’t miss the other parts of our ‘Guide to complete Zero Trust’ blog series:
- What is ‘Zero Trust’ and why do we need it? (part 1)
- Cloud, Mobile and Remote-work as Drivers of the Zero Trust Approach (part 2)
- How Forrester and Google made Zero Trust mainstream? (part 3)
If you would like to learn in detail about “Complete Zero Trust – The Paradigm Shift in IT Security”, our whitepaper is now available to you!
